270
Appendix E. Session Limit and Session Log
Session Limit
To prevent ill-behaved clients or malicious software from using up system’s connection resources,
administrators will have to restrict the number of concurrent sessions that a user can establish.
The maximum number of concurrent sessions (TCP and UDP) for each user can be specified in the Global
policy, which applies to authenticated users, users on a non-authenticated port, privileged users, and
clients in DMZ zones.
When the number of a user’s sessions reaches the session limit (a choice of Unlimited, 10, 25, 50, 100,
200, 350, and 500), the user will be implicitly suspended upon receipt of any new connection request. In
this case, a record will be logged to the SYSLOG server specified in the Email & SYSLOG.
Since this basic protection mechanism may not be able to protect the system from all malicious DoS
attacks, it is strongly recommended to build some immune capabilities (such as IDS or IPS solutions) in the
network deployment to protect the network in daily operation.
Session Log
The system can record connection details of each user accessing the Internet. In addition, the log data can be
sent out to a specified SYSLOG Server, Email Box or FTP Server based on pre-defined interval time.
The following table shows the fields of a session log record.
Field
Description
Date and Time
The date and time that the session is established
Session Type
[New]: This is the newly established session.
[Blocked]: This session is blocked by a Firewall rule.
Username
The account name (with postfix) of the user; It shows “N.A.” if the user
or device does not need to log in with a username. For example, the
user or device is on a non-authenticated port or on the privileged
MAC/IP list. Note: Only 31 characters are available for the
combination of Session Type plus Username. Please change the
account name accordingly, if the name is not identifiable in the record.
Protocol
The communication protocol of session: TCP or UDP
MAC
The MAC address of the user’s computer or device
SIP
The source IP address of the user’s computer or device
SPort
The source port number of the user’s computer or device
DIP
The destination IP address of the user’s computer or device
DPort
The destination port number of the user’s computer or device
Содержание WHG-505
Страница 1: ...LevelOne WHG 505 Secure WLAN Controller User Manual V1 00...
Страница 19: ...13...
Страница 33: ...27...
Страница 57: ...51...
Страница 66: ...60...
Страница 91: ...85 6 Local Area AP Management...
Страница 115: ...109...
Страница 121: ...115 AP status Client List and WDS List information listed are collected from the remote AP via SNMP...
Страница 129: ...123...
Страница 147: ...141...
Страница 172: ...166...
Страница 188: ...182 5 2 2 HW To view Hardware Status go to Status HW This tab page displays the system s hardware usage information...
Страница 198: ...192...
Страница 211: ...205...
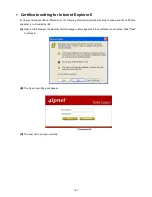
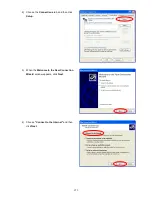
Страница 266: ...260 5 Click Install Certificate 6 Click Next...
Страница 300: ...294 2 Port Location Mapping To configure Port Location Mapping go to System Port Location Mapping Configure...
Страница 307: ...301...