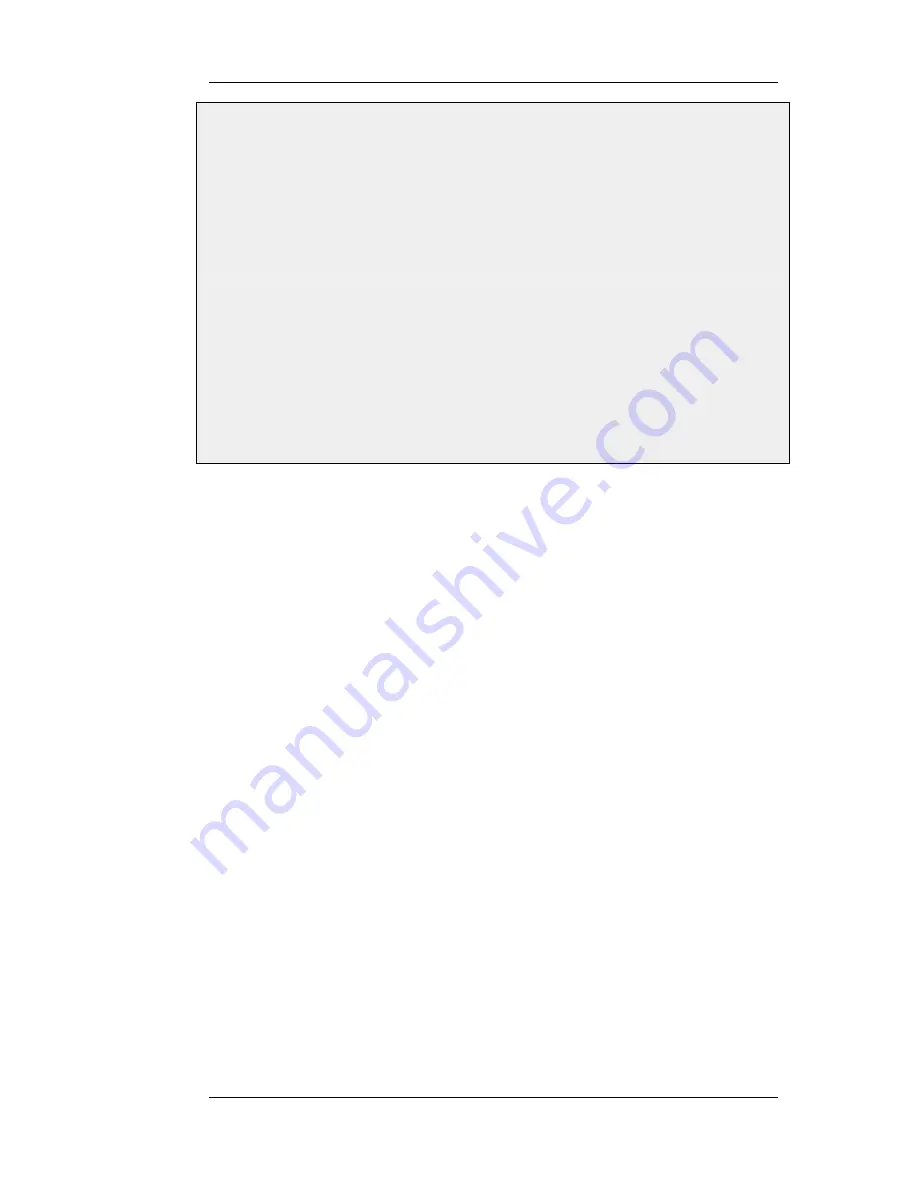
2.
Specify a name for the pipe, for example std-out
3.
Enter 2000 in Total textbox
4.
Click OK
After creating a pipe for outbound bandwidth control, add it to the forward pipe chain of the rule created in the
previous example:
CLI
gw-world:/> set PipeRule Outbound ForwardChain=std-out
Web Interface
1.
Go to Traffic Management > Traffic Shaping > Pipe Rules
2.
Right-click on the pipe rule you created in the previous example and choose Edit
3.
Under the Traffic Shaping tab, select std-out in the Forward Chain list
4.
Click OK
This results in all outbound connections being limited to 2 Mbps in each direction.
10.1.5. Creating Differentiated Limits with Chains
In the previous examples a static traffic limit for all outbound connections was applied. What if we
want to limit web surfing more than other traffic? We could set up two "surfing" pipes for inbound
and outbound traffic. However, we most likely will not need to limit outbound traffic because
surfing usually consists of short outbound requests followed by long inbound answers. Let's assume
the total bandwidth limit is 250 kbps and 125 kbps of that is to be allocated to web surfing inbound
traffic. A surf-in pipe is therefore setup for inbound traffic with a 125 kbps limit.
Next, a new Pipe Rule is set up for surfing that uses the surf-in pipe and it is placed before the rule
that directs "everything else" through the std-in pipe. That way surfing traffic goes through the
surf-in pipe and everything else is handled by the rule and pipe created earlier.
Unfortunately this will not achieve the desired effect, which is allocating a maximum of 125 kbps to
inbound surfing traffic as part of the 250 kbps total. Inbound traffic will pass through one of two
pipes: one that allows 250 kbps, and one that allows 125 kbps, giving a possible total of 375 kbps of
inbound traffic.
To solve this, we create a chain of the surf-in pipe followed by the std-in pipe in the surfing traffic
Pipe Rule. Inbound surf traffic will now first pass through surf-in and be limited to a maximum of
125 kbps. Then, it will pass through the std-in pipe along with other inbound traffic, which will
apply the 250 kbps total limit. If surfing uses the full limit of 125 kbps, those 125 kbps will occupy
half of the std-in pipe leaving 125 kbps for the rest of the traffic. If no surfing is taking place then
all of the 250 kbps allowed through std-in will be available for other traffic.
This is not a bandwidth guarantee for web browsing but it is a 125 kbps bandwidth guarantee for
everything except web browsing. For web browsing the normal rules of first-come, first-forwarded
will apply when competing for bandwidth. This may mean 125 kbps, but it may also mean much
slower speed if the connection is flooded.
Setting up pipes in this way only puts limits on the maximum values for certain traffic types. It does
not give priorities to different types of competing traffic.
10.1.6. Precedences
All packets that pass through NetDefendOS traffic shaping pipes have a precedence. In the
examples so far, precedences have not been explicitly set and so all packets have had the same
10.1.5. Creating Differentiated Limits
with Chains
Chapter 10. Traffic Management
383
Содержание 800 - DFL 800 - Security Appliance
Страница 24: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 24 ...
Страница 69: ...2 6 4 Restore to Factory Defaults Chapter 2 Management and Maintenance 69 ...
Страница 121: ...3 9 DNS Chapter 3 Fundamentals 121 ...
Страница 166: ...interfaces without an overriding IGMP Setting Default 1 000 4 6 4 Advanced IGMP Settings Chapter 4 Routing 166 ...
Страница 181: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 181 ...
Страница 192: ...5 5 IP Pools Chapter 5 DHCP Services 192 ...
Страница 282: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 282 ...
Страница 300: ...mechanism 7 3 7 SAT and FwdFast Rules Chapter 7 Address Translation 300 ...
Страница 301: ...7 3 7 SAT and FwdFast Rules Chapter 7 Address Translation 301 ...
Страница 303: ... Changed on a regular basis such as every three months 8 1 Overview Chapter 8 User Authentication 303 ...
Страница 318: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 318 ...
Страница 322: ...ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 322 ...
Страница 377: ...Management Interface Failure with VPN Chapter 9 VPN 377 ...
Страница 408: ...10 4 6 SLB_SAT Rules Chapter 10 Traffic Management 408 ...
Страница 419: ...11 5 HA Advanced Settings Chapter 11 High Availability 419 ...
Страница 426: ...12 3 5 Limitations Chapter 12 ZoneDefense 426 ...
Страница 449: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 449 ...




































