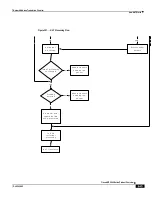
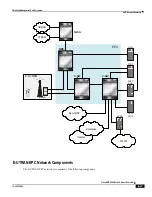
Network Address Translation Overview
▀ NAT Feature Overview
▄ Cisco ASR 5000 Series Product Overview
OL-22938-02
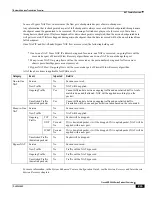
nat-rlm-max-cur-port-chunk-used: Maximum port chunks used by active subscribers.
nat-rlm-port-chunk-size: Size of the port chunk in the NAT realm.
nat-rlm-port-chunk-average-usage-tcp: Average TCP port usage in the allocated TCP ports, i.e. out of allocated
TCP ports how many got used. Not percentage value.
nat-rlm-port-chunk-average-usage-udp: Average UDP port usage in the allocated UDP ports, i.e. out of allocated
UDP ports how many got used. Not percentage value.
nat-rlm-port-chunk-average-usage-others: Average other (ICMP or GRE) port usage in the allocated other ports,
i.e. out of allocated ‗other‘ ports how many got used. Not percentage value.
Alarms
Alert threshold values can be specified to generate alarms for NAT IP pools. To specify realm-specific threshold limits
(pool-used, pool-free, pool-release, and pool-hold) ―alert-threshold‖ NAT IP pool parameter can be used, or it can also
be specified across context. These thresholds can be specified to any number of NAT IP pools.
In case of many-to-one NAT, it is possible to specify port-chunks usage threshold per NAT IP pool. This threshold
value is applicable to all many-to-one NAT IP pools across the system. However, note that alarms are only generated for
the first 100 many-to-one NAT IP pools from an alphabetical list of all NAT IP pools.
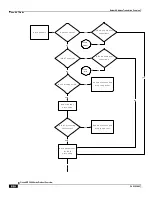
Session Recovery and ICSR
In session recovery, as part of the Private IP assigned to the subscriber:
The public IP address used for the subscriber is recovered. The NAT IP address being used by the subscriber can
be on-demand or not-on-demand. In case of many-to-one NAT, the port-chunks associated with the NAT IP
address for the subscriber needs to check-pointed as well.
In case Bypass NAT feature is used, then the private IP flow needs to be recovered.
To be recovered the NAT IP addresses need to be checkpointed. The checkpointing can be:
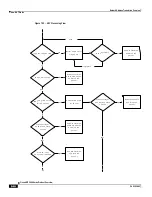
Full Checkpoint
Micro Checkpoint
To recover the bypass NAT flow, the bypass flow needs to be checkpointed. The checkpointing of Bypass NAT flow
can be:
Full Checkpoint
Micro Checkpoint
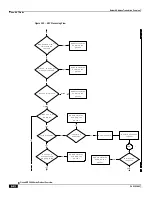
In case of not-on-demand, the NAT IP address being used by the subscriber is known after call setup. This gets
checkpointed as part of the normal full checkpoint. In case of on-demand NAT, the NAT IP address being used by the
subscriber is known only in the data-path. This will be checkpointed as part of micro checkpoint.
In case of many-to-one NAT, the port-chunks being used will always be checkpointed as part of micro checkpoint.
Содержание ASR 5000 Series
Страница 1: ......
Страница 26: ......
Страница 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 50: ......
Страница 58: ......
Страница 67: ...Product Service and Feature Licenses Default Licenses Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 68: ......
Страница 126: ......
Страница 138: ......
Страница 146: ......
Страница 218: ......
Страница 236: ......
Страница 356: ......
Страница 374: ......
Страница 422: ......
Страница 496: ......
Страница 572: ......
Страница 654: ......
Страница 700: ......
Страница 726: ......
Страница 784: ......
Страница 816: ......
Страница 839: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 841: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 844: ......
Страница 906: ......
Страница 926: ......
Страница 942: ......
Страница 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Страница 966: ......
Страница 967: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 31 Safety Electrical and Environmental Certifications ...
Страница 972: ......