CDMA2000 Wireless Data Services
Understanding Simple IP and Mobile IP ▀
Cisco ASR 5000 Series Product Overview ▄
OL-22938-02
IP in IP tunnels basically encapsulate one IP packet within another using a simple encapsulation technique. To
encapsulate an IP datagram using IP in IP encapsulation, an outer IP header is inserted before the datagram's existing IP
header. Between them are other headers for the path, such as security headers specific to the tunnel configuration. Each
header chains to the next using IP Protocol values. The outer IP header Source and Destination identify the ―endpoints‖
of the tunnel. The inner IP header Source and Destination identify the original sender and recipient of the datagram,
while the inner IP header is not changed by the encapsulator, except to decrement the TTL, and remains unchanged
during its delivery to the tunnel exit point. No change to IP options in the inner header occurs during delivery of the
encapsulated datagram through the tunnel. If needed, other protocol headers such as the IP Authentication header may
be inserted between the outer IP header and the inner IP header.
The Mobile IP working group has specified the use of encapsulation as a way to deliver datagrams from an MN's HA to
an FA, and conversely from an FA to an HA, that can deliver the data locally to the MN at its current location.
GRE tunnels
The Generic Routing Encapsulation (GRE) protocol performs encapsulation of IP packets for transport across disparate
networks. One advantage of GRE over earlier tunneling protocols is that any transport protocol can be encapsulated in
GRE. GRE is a simple, low overhead approach—the GRE protocol itself can be expressed in as few as eight octets as
there is no authentication or tunnel configuration parameter negotiation. GRE is also known as IP Protocol 47.
Important:
The chassis simultaneously supports GRE protocols with key in accordance with RFC-1701/RFC-
2784 and ―Legacy‖ GRE protocols without key in accordance to RFC-2002.
Another advantage of GRE tunneling over IP-in-IP tunneling is that GRE tunneling can be used even when conflicting
addresses are in use across multiple contexts (for the tunneled data).
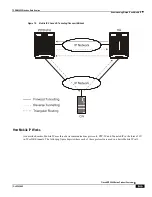
Communications between the FA and HA can be done in either the forward or reverse direction using the above
protocols. Additionally, another method of routing information between the FA and various content servers used by the
HA exists. This method is called Triangular Routing. Each of these methods is explained below.
Forward Tunneling
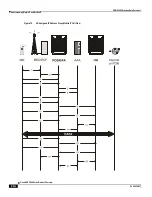
In the wireless IP world, forward tunneling is a tunnel that transports packets from the packet data network towards the
MN. It starts at the HA and ends at the MN's care-of address. Tunnels can be as simple as IP-in-IP tunnels, GRE
tunnels, or even IP Security (IPSec) tunnels with encryption. These tunnels can be started automatically, and are
selected based on the subscriber's user profile.
The following figure shows an example of how forward tunneling is performed.
Reverse Tunneling
A reverse tunnel starts at the MN's care-of address, which is the FA, and terminates at the HA.
When an MN arrives at a foreign network, it listens for agent advertisements and selects an FA that supports reverse
tunnels. The MN requests this service when it registers through the selected FA. At this time, the MN may also specify a
delivery technique such as Direct or the Encapsulating Delivery Style.
Using the Direct Delivery Style, which is the default mode for the system, the MN designates the FA as its default
router and sends packets directly to the FA without encapsulation. The FA intercepts them, and tunnels them to the HA.
Using the Encapsulating Delivery Style, the MN encapsulates all its outgoing packets to the FA. The FA then de-
encapsulates and re-tunnels them to the HA, using the FA's care-of address as the entry-point for this new tunnel.
Содержание ASR 5000 Series
Страница 1: ......
Страница 26: ......
Страница 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 50: ......
Страница 58: ......
Страница 67: ...Product Service and Feature Licenses Default Licenses Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 68: ......
Страница 126: ......
Страница 138: ......
Страница 146: ......
Страница 218: ......
Страница 236: ......
Страница 356: ......
Страница 374: ......
Страница 422: ......
Страница 496: ......
Страница 572: ......
Страница 654: ......
Страница 700: ......
Страница 726: ......
Страница 784: ......
Страница 816: ......
Страница 839: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 841: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 844: ......
Страница 906: ......
Страница 926: ......
Страница 942: ......
Страница 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Страница 966: ......
Страница 967: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 31 Safety Electrical and Environmental Certifications ...
Страница 972: ......