CDMA2000 Wireless Data Services
▀ Features and Functionality - Optional Enhanced Software Features
▄ Cisco ASR 5000 Series Product Overview
OL-22938-02
RFC 2409, The Internet Key Exchange (IKE)
RFC-3193, Securing L2TP using IPSEC, November 2001
Description
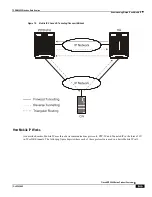
IP Security (IPSec) is a suite of protocols that interact with one another to provide secure private communications across
IP networks. These protocols allow the system to establish and maintain secure tunnels with peer security gateways.
IPSec can be implemented on the system for the following applications:
PDN Access: Subscriber IP traffic is routed over an IPSec tunnel from the system to a secure gateway on the
Packet Data Network (PDN) as determined by Access Control List (ACL) criteria.
Mobile IP: Mobile IP control signals and subscriber data is encapsulated in IPSec tunnels that are established
between Foreign Agents (FAs) and Home Agents (HAs) over the Pi interfaces.
Once an IPSec tunnel is established between an FA and HA for a particular subscriber, all new Mobile IP
sessions using the same FA and HA are passed over the tunnel regardless of whether or not IPSec is supported
for the new subscriber sessions. Data for existing Mobile IP sessions is unaffected.
L2TP: L2TP-encapsulated packets are routed from the system to an LNS/secure gateway over an IPSec tunnel.
Important:
For more information on IPSec support, refer IP Security chapter in System Enhanced Feature
Configuration Guide.
Traffic Policing and Rate Limiting
Allows the operator to proportion the network and support Service-level Agreements (SLAs) for customers
Description
The Traffic-Policing/Shaping feature enables configuring and enforcing bandwidth limitations on individual PDP
contexts of a particular 3GPP traffic class. Values for traffic classes are defined in 3GPP TS 23.107 and are negotiated
with the SGSN during PDP context activation using the values configured for the subscriber on the PDSN.
Configuration and enforcement is done independently on the downlink and the uplink directions for each of the 3GPP
traffic classes. Configuration is on a per-subscriber basis, but may be overridden for individual subscribers or subscriber
tiers during RADIUS authentication/authorization.
A Token Bucket Algorithm (a modified trTCM, as specified in RFC2698) is used to implement the Traffic-Policing
feature. The algorithm measures the following criteria when determining how to mark a packet.
Committed Data Rate (CDR):
The guaranteed rate (in bits per second) at which packets may be transmitted/received for
the subscriber during the sampling interval.
Peak Data Rate (PDR):
The maximum rate (in bits per second) that packets may be transmitted/received for the
subscriber during the sampling interval.
Содержание ASR 5000 Series
Страница 1: ......
Страница 26: ......
Страница 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 50: ......
Страница 58: ......
Страница 67: ...Product Service and Feature Licenses Default Licenses Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 68: ......
Страница 126: ......
Страница 138: ......
Страница 146: ......
Страница 218: ......
Страница 236: ......
Страница 356: ......
Страница 374: ......
Страница 422: ......
Страница 496: ......
Страница 572: ......
Страница 654: ......
Страница 700: ......
Страница 726: ......
Страница 784: ......
Страница 816: ......
Страница 839: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 841: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 844: ......
Страница 906: ......
Страница 926: ......
Страница 942: ......
Страница 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Страница 966: ......
Страница 967: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 31 Safety Electrical and Environmental Certifications ...
Страница 972: ......