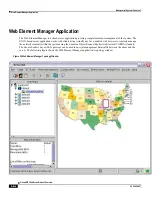
ASN Gateway Overview
Supported Features ▀
Cisco ASR 5000 Series Product Overview ▄
OL-22938-02
EAP-identity response. It subsequently unpacks EAP messages over the R6 interface and transfers them via RADIUS or
Diameter signaling to the AAA server.
EAP authentication provide multiple authentication methods that can be tailored to the operator‘s preference toward
user-level, device-level, or user- and device-level network authorization. At the H-AAA server in Home Network
Service Provider (H-NSP), device-level authentication in a roaming application guards against unauthorized network
access by users with stolen access devices.
Supported RADIUS Methods
ASN Gateway supports following EAP authentication and authorization methods using RADIUS:
EAP-Pre-shared Key (EAP-PSK)
EAP-Transport Layer Security (EAP-TLS)
EAP-Tunneled Transport Layer Security (EAP-TTLS)
EAP-Authentication and Key Agreement (EAP-AKA)
EAP-Pre-shared Key (EAP-PSK)
EAP-PSK is a symmetric mutual authentication method that uses manually provisioned pre-shared keys between an
EAP client on an access device and an EAP server component on AAA. The size of the pre-shared key can be up to 256
bytes.
EAP-Transport Layer Security (EAP-TLS)
EAP-TLS is an asymmetric authentication method that uses X.509 digital certificates, for example public/private key
pairs, and enables device-based authentication.
EAP-Tunneled Transport Layer Security (EAP-TTLS)
EAP-TTLS is a multi-level authentication scheme to enable device and user-based authentication. The first level
handshake provides device-level authentication and uses the same encryption and ciphering algorithms as EAP-TLS.
The secure connection established through the first level handshake is then extended with MS-CHAP-V2 authentication
to verify user credentials. As with other EAP methods, successful EAP transactions at AAA result in a Master Session
Key (MSK) that is returned over an encrypted connection. The ASN Gateway uses the key to generate a derivative key
for securing the air interface between ASN and user access device.
EAP-Authentication and Key Agreement (EAP-AKA)
EAP-AKA uses symmetric cryptography based on pre-shared private client/server keys and challenge-response
mechanisms similar to other EAP methods. It verifies credentials for users of Removable User Identity Modules (R-
UIMs).
Содержание ASR 5000 Series
Страница 1: ......
Страница 26: ......
Страница 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 50: ......
Страница 58: ......
Страница 67: ...Product Service and Feature Licenses Default Licenses Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 68: ......
Страница 126: ......
Страница 138: ......
Страница 146: ......
Страница 218: ......
Страница 236: ......
Страница 356: ......
Страница 374: ......
Страница 422: ......
Страница 496: ......
Страница 572: ......
Страница 654: ......
Страница 700: ......
Страница 726: ......
Страница 784: ......
Страница 816: ......
Страница 839: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 841: ...Network Address Translation Overview How NAT Works Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Страница 844: ......
Страница 906: ......
Страница 926: ......
Страница 942: ......
Страница 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Страница 966: ......
Страница 967: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 31 Safety Electrical and Environmental Certifications ...
Страница 972: ......