51
Chapter 7: Configuring the Router’s Web-Based Utility
Diagnostics
Dual-Band Wireless Access Point
Notification Qeue Length
•
Log queue Length. Enter the
number
of entries in the log queue in the field.
•
Log Time Threshold. Enter the
time
for the threshold in the field.
Alert Log
Select the alert log that you want to ______. Select Syn Flooding, IP Spoofing, Win Nuke, Ping of Death, or
Unauthorized Login attempt.
General Log.
Select the ________. Select System Error Messages, Deny Policies, Allow Policies, Content Filtering, Data
Inspection, authorized Login, or Configuration Changes.
When finished making your changes on this tab, click the
Save Settings
button to save these changes, or click
the
Cancel Changes
button to undo your changes.
Diagnostics
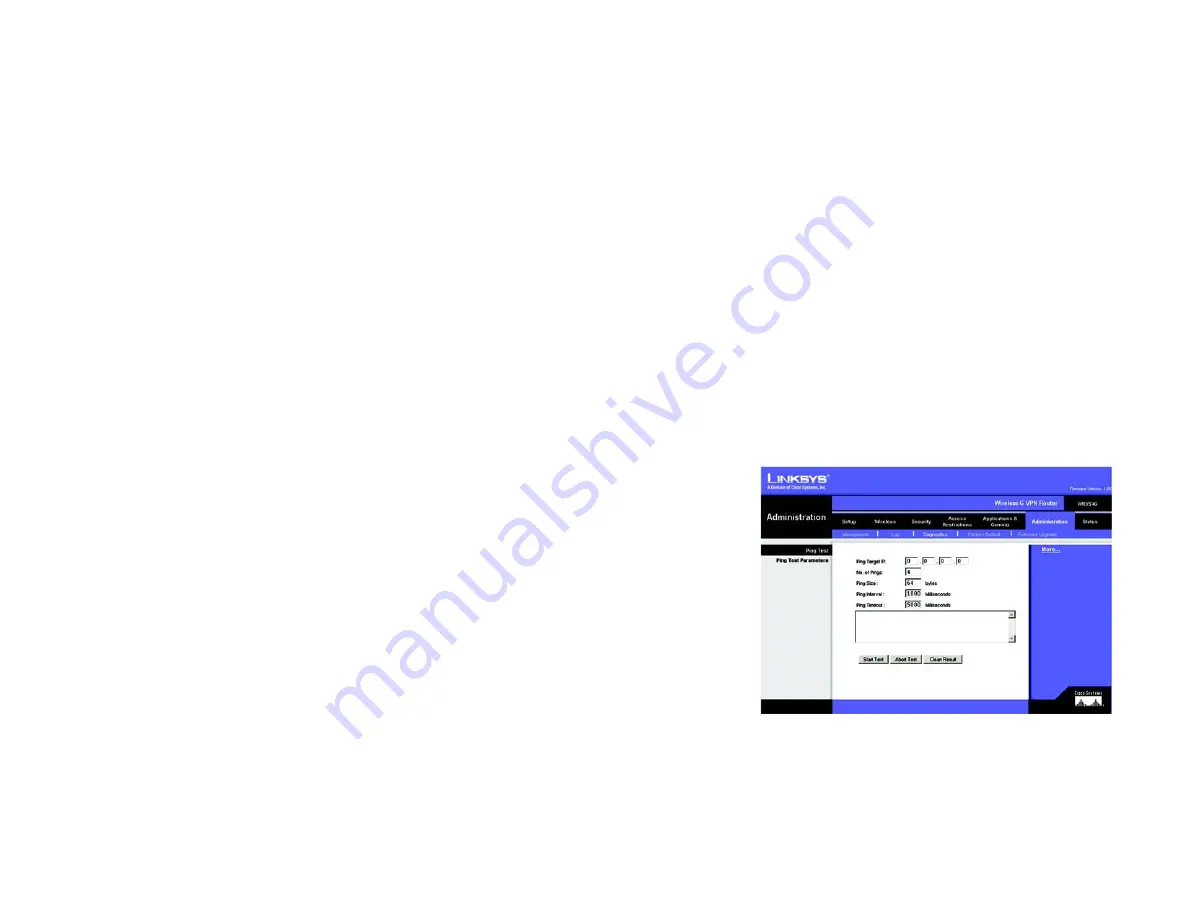
Ping Test
Ping Test Parameters
Ping Target IP. Enter the IP Address that you want to ping in the field.
No. of Pings. Enter the number of times that you want to ping.
Ping Size. Enter the size of the ____.
Ping Interval. Enter the ping interval in Milliseconds.
Ping Timeout. Enter the time in Milliseconds.
Click the Start Test button to start the Ping Test. Click the Abort Test button to stop the test. Click the Clean Result
button if _____. The results of the test will display in the window.
Figure 7-32:
















































