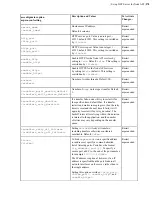
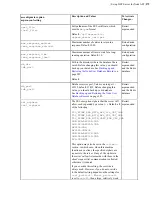
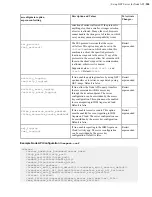
| Set up HST Server for Node API |
288
b.
the certificates bundle, which includes the root certificate
If you do not have a certificates bundle from the CA, the contents of
aspera_server_cert.chain
must
consist of the following, in the order shown:
a.
the server certificate
b.
any chained or intermediary certificates from the CA in order of ascending authority, for example:
intermediary certificate 1
intermediary certificate 2
intermediary certificate 3
c.
the root certificate from the CA
5.
Restart asperacentral, asperanoded, and asperahttpd:
# service asperacentral restart
# service asperahttpd restart
# service asperanoded restart
6.
Verify the certificates by using OpenSSL.
a) Test that you can connect to asperanoded by running the following command:
# /opt/aspera/bin/openssl s_client -connect
myserver
:9092
This example assumes that you are using the default node port (HTTPS 9092). Replace
myserver
with the IP
address or hostname of your server.
The command returns
0
for success or
1
for failure.
Output examples:
Success:
The following sample output shows that verification was successful because
verify return
is 0.
depth=2 C = US, O = "VeriSign, Inc.", OU = VeriSign Trust Network, OU =
"(c) 2006 VeriSign, Inc. -
For authorized use only", CN = VeriSign Class 3Public Primary
Certification Authority - G5
verify error:num=20:unable to get local issuer certificate
verify return:0
Failure:
The following sample output shows that verification failed because
verify return
is 1.
depth=0 C = US, ST = California, L = Emeryville, O = IBM, OU = Aspera
Inc IT Department, CN = *.asperafiles.com
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = US, ST = California, L = Emeryville, O = IBM, OU = Aspera
Inc IT Department, CN = *.asperafiles.com
verify error:num=27:certificate not trusted
verify return:1
depth=0 C = US, ST = California, L = Emeryville, O = IBM, OU = Aspera
Inc IT Department, CN = *.asperafiles.com
verify error:num=21:unable to verify the first certificate
verify return:1
Note:
You must see as many elements in the output as there are certificates in the chain. In the following
examples there is one root certificate and two chained certificates, so the output must show three elements to
prove the installation was successful.