SH-E514TR1 10 Gigabit Ethernet SmartPro Switch User Manual
58
If the forwarding domain of an interface is empty, then there is no restriction on Layer 2 forwarding of packets received
by the port.
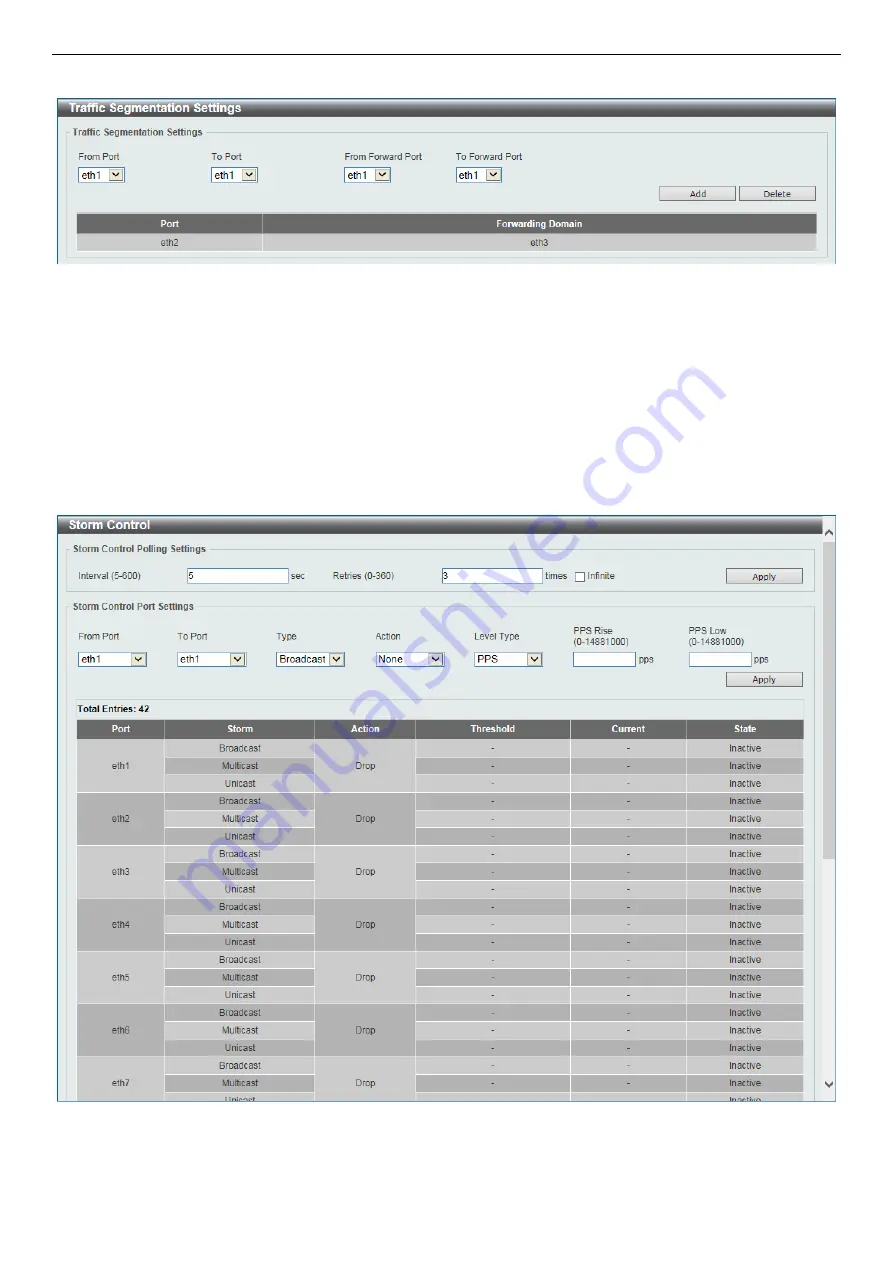
Figure 12-4 Traffic Segmentation Settings
The fields that can be configured are described below:
From Port / To Port:
Select the receiving port range used for the configuration here.
From Forward Port / To Forward Port:
Select the forward port range used for the configuration here.
Click
Add
to add a new entry based on the information entered.
Click
Delete
to remove a new entry based on the information entered.
Storm Control
This window is used to view and configure the storm control settings.
Figure 12-5 Storm Control
The fields that can be configured are described below:









































