20
Chapter 5: Setting up the Wireless-G Broadband Router
Using the Setup Wizard
Wireless-G Broadband Router
Telstra
Connection
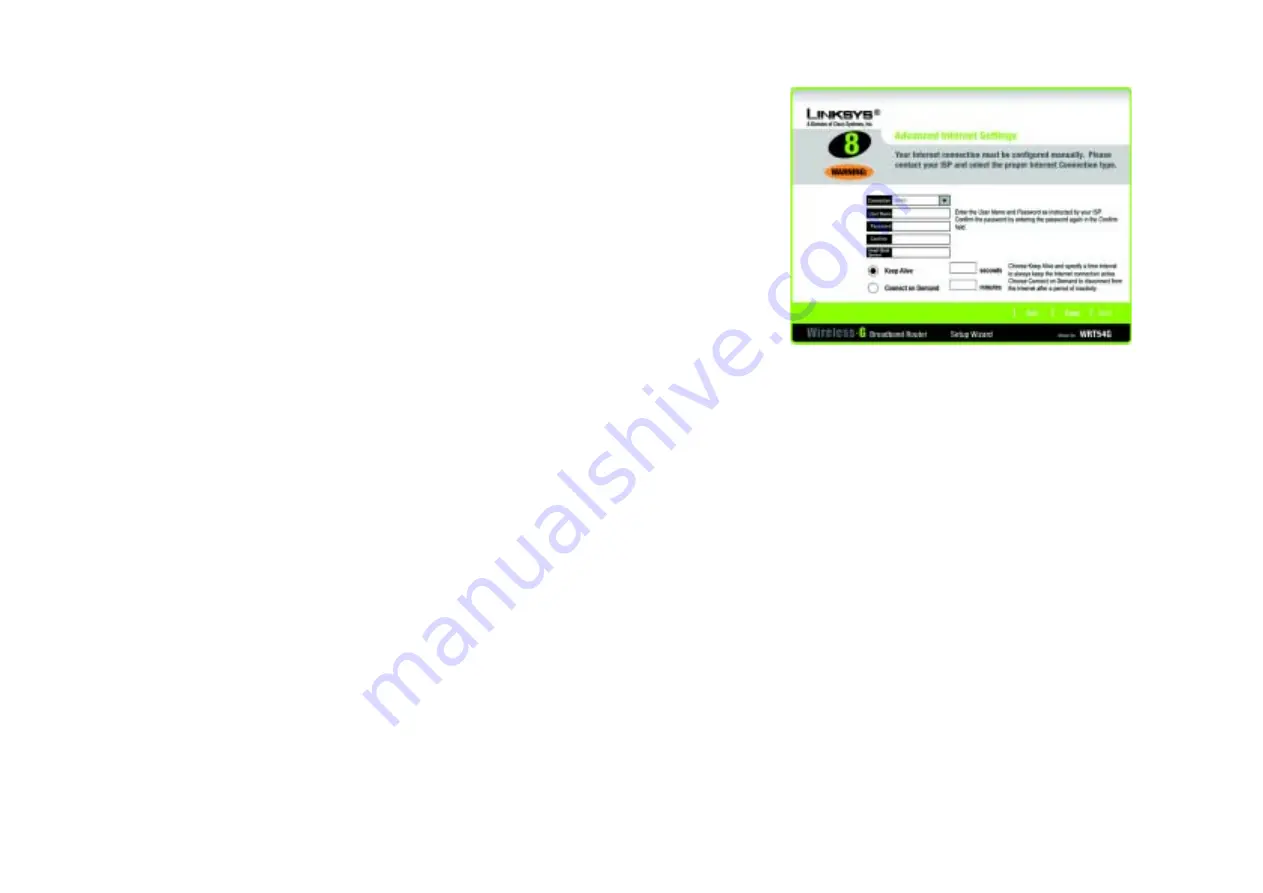
- Telstra is a service used in Australia only. If you are using this service, select
Telstra
from the
drop-down menu.
User Name
- Enter the User Name provided by your ISP.
Password
- Enter the Password provided by your ISP.
Confirm
- To confirm the Password, enter it again in this field.
Heart Beat Server
- Enter the IP address of the Heart Beat Server server you are using (this should be
provided by your ISP).
Keep Alive
- If you want the Router to periodically check your Internet connection, select
Keep Alive
. Then
specify how often you want the Router to check the Internet connection. If the connection is down, the Router
will automatically re-establish your connection.
Connect on Demand
- If you want the Router to end the Internet connection after it has been inactive for a
period of time, select
Connect on Demand
and designate the number of minutes you want that period of
inactivity to last.
Click the
Next
button to continue or the
Back
button to return to the previous screen.
Figure 5-16: Setup Wizard’s Advanced Internet Settings -
Telstra Screen






























