Authentication Types
Configuring Authentication Types
22
Cisco 3200 Series Wireless MIC Software Configuration Guide
3.
Configure the non-root bridge to act as a LEAP client.
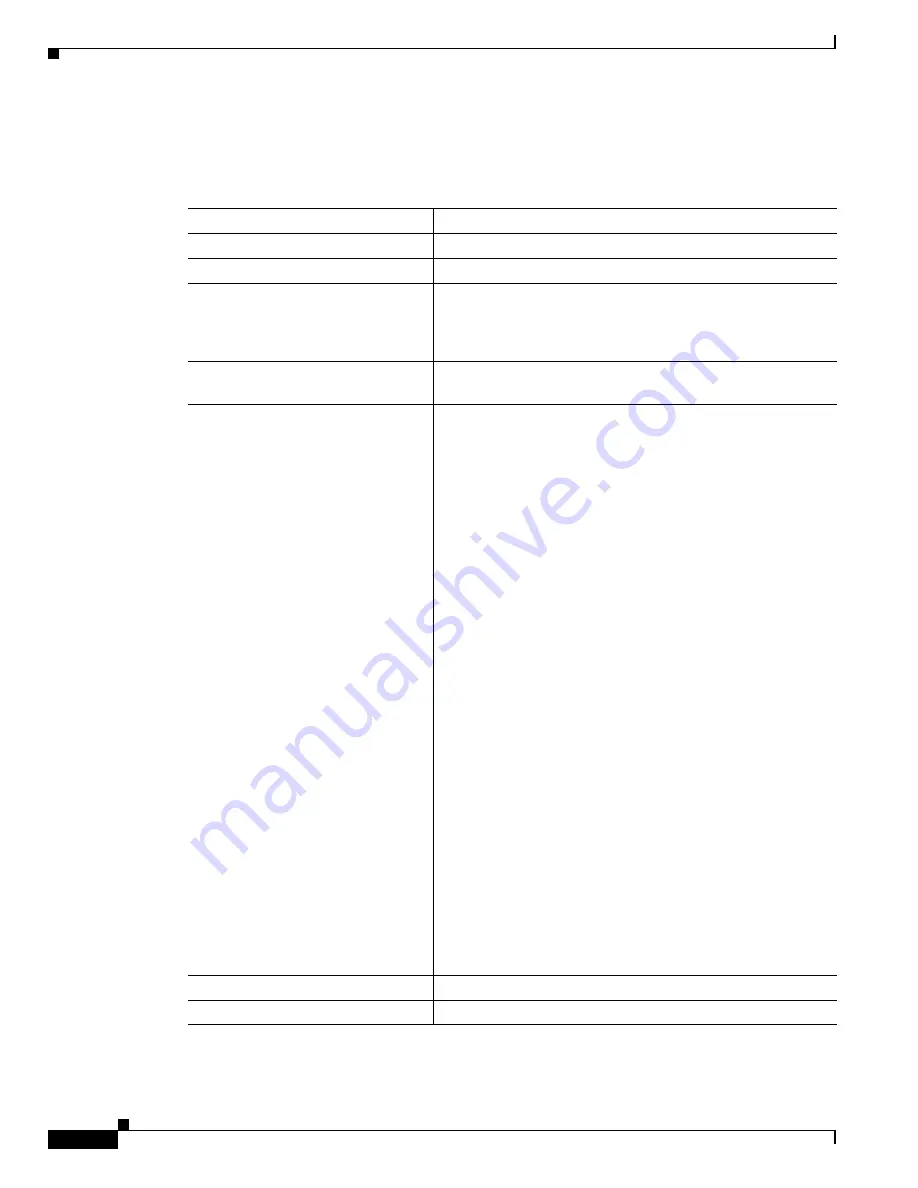
Beginning in privileged EXEC mode, follow these steps to configure authentication types for SSIDs on
the non-root side:
Command
Purpose
Step 1
configure terminal
Enters global configuration mode.
Step 2
dot11 ssid
ssid-string
Enters global SSID mode.
Step 3
authentication network-eap
list-name
(Optional) Sets the authentication type for the SSID to use
LEAP for authentication and key distribution. Cisco bridges
support only LEAP, while other wireless clients may support
other EAP methods such as EAP, PEAP, or TLS.
Step 4
authentication client username
username
password
password
Specifies the user name and password for the LEAP client.
Step 5
authentication key-management
{[
wpa
]
[
cckm
]} [
optional
]
(Optional) Sets the key management type for the SSID to WPA,
CCKM, or both. If you use the
optional
keyword, non-root
bridges not configured for WPA or CCKM can use this SSID.
If you do not use the
optional
keyword, only WPA or CCKM
bridges are allowed to use the SSID.
To enable CCKM for an SSID, you must also enable
Network-EAP authentication. To enable WPA for an SSID, you
must also enable open authentication or Network-EAP or both.
Note
Only 802.11b and 802.11g radios support WPA and
CCKM simultaneously.
Note
Before you can enable CCKM or WPA, you must set
the encryption mode for the SSID’s VLAN to one of the
cipher suite options. To enable both CCKM and WPA,
you must set the encryption mode to a cipher suite that
includes TKIP. See the
“Cipher Suites and WEP”
document for instructions on configuring the VLAN
encryption mode.
Note
If you enable WPA for an SSID without a pre-shared
key, the key management type is WPA. If you enable
WPA with a pre-shared key, the key management type
is WPA-PSK. See the
“Configuring Additional WPA
Settings” section on page 23
for instructions on
configuring a pre-shared key.
Note
To support CCKM, your root device must interact with
the WDS device on your network. See the
“Configuring
the Root Device to Interact with the WDS Device”
section on page 23
for instructions on configuring your
root device to interact with your WDS device.
Step 6
end
Returns to privileged EXEC mode.
Step 7
copy running-config startup-config
(Optional) Saves your entries in the configuration file.






























