184
VPN
A
virtual private network
(
VPN
) is a private network that interconnects remote (and often
geographically separate) networks through primarily public communication infrastructures such as
the Internet. VPNs provide security through tunneling protocols and security procedures such as
encryption. For example, a VPN could be used to securely connect the branch offices of an
organization to a head office network through the public Internet.
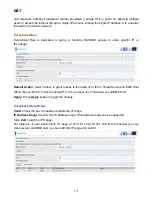
IPSec
Internet Protocol Security
(
IPsec
) is a protocol suite for securing Internet Protocol (IP)
communications by authenticating and encrypting each IP packet of a communication session. IPsec
also includes protocols for establishing mutual authentication between agents at the beginning of the
session and negotiation of cryptographic keys to be used during the session.
IPsec is an end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite.
It can be used in protecting data flows between a pair of security gateways (
network-to-network
), or
between a security gateway and a host (
network-to-host
).
Note:
A maximum of 16 sessions for IPSec.
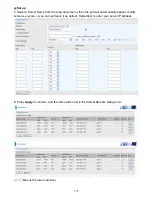
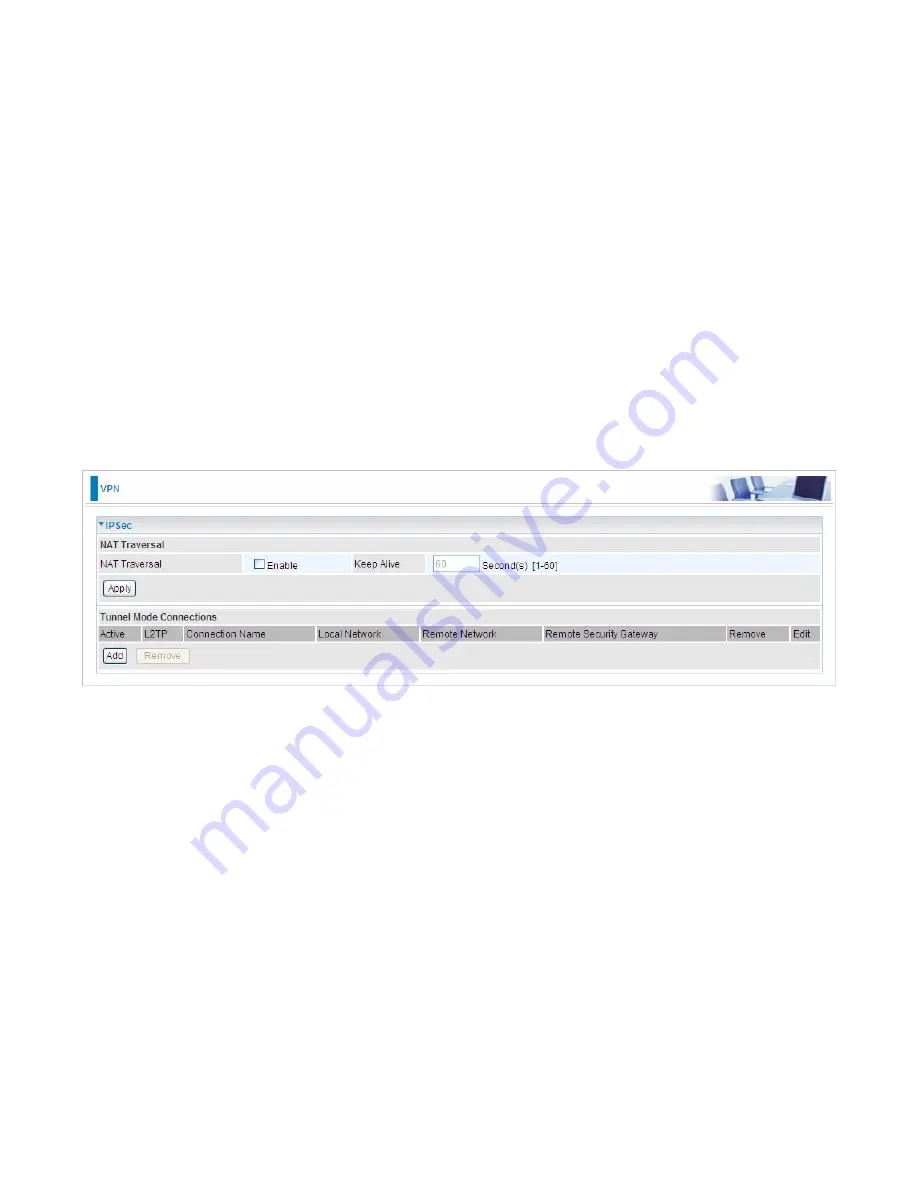
NAT Traversal
NAT Traversal:
This directive enables use of the NAT-Traversal IPsec extension (NAT-T). NAT-T
allows one or both peers to reside behind a NAT gateway (i.e., doing address- or port-translation).
Keep Alive:
Type the interval time(sec) for sending packets to keep the NAT Traversal alive.
Click
Apply
to save and apply your settings.
Summary of Contents for 7800DX
Page 19: ...15 3G LTE Router mode ...
Page 37: ...33 Click link 192 168 1 254 it will lead you to the following page ...
Page 40: ...36 Click 192 168 1 254 it will lead you to the following page ...
Page 43: ...39 Click 192 168 1 254 it will lead you to the following page ...
Page 99: ...95 Configure AP as Enrollee Add Registrar with PIN Method 1 Set AP to Unconfigured Mode ...
Page 143: ...139 Accessing mechanism of Storage In your computer Click Start Run enter 192 168 1 254 ...
Page 145: ...141 Access the folder public ...
Page 148: ...144 Step 2 Click Add a Printer Step 3 Click Add a network wireless or Bluetooth printer ...
Page 159: ...155 Rule inactive ...
Page 186: ...182 ALG The ALG Controls enable or disable protocols over application layer ...
Page 194: ...190 ...
Page 197: ...193 ...
Page 204: ...200 5 Input the account user name and password and press Create ...
Page 205: ...201 6 Connect to the server ...
Page 206: ...202 7 Successfully connected ...
Page 208: ...204 ...
Page 219: ...215 4 Input Internet address and Destination name for this connection and press Next ...
Page 220: ...216 5 Input the account user name and password and press Create ...
Page 238: ...234 2 ipoe_eth0 with DDNS www hometest1 com using username password test test ...
Page 251: ...247 Click Apply to confirm your settings ...
Page 262: ...258 Example Ping www google com ...
Page 263: ...259 Example trace www google com ...