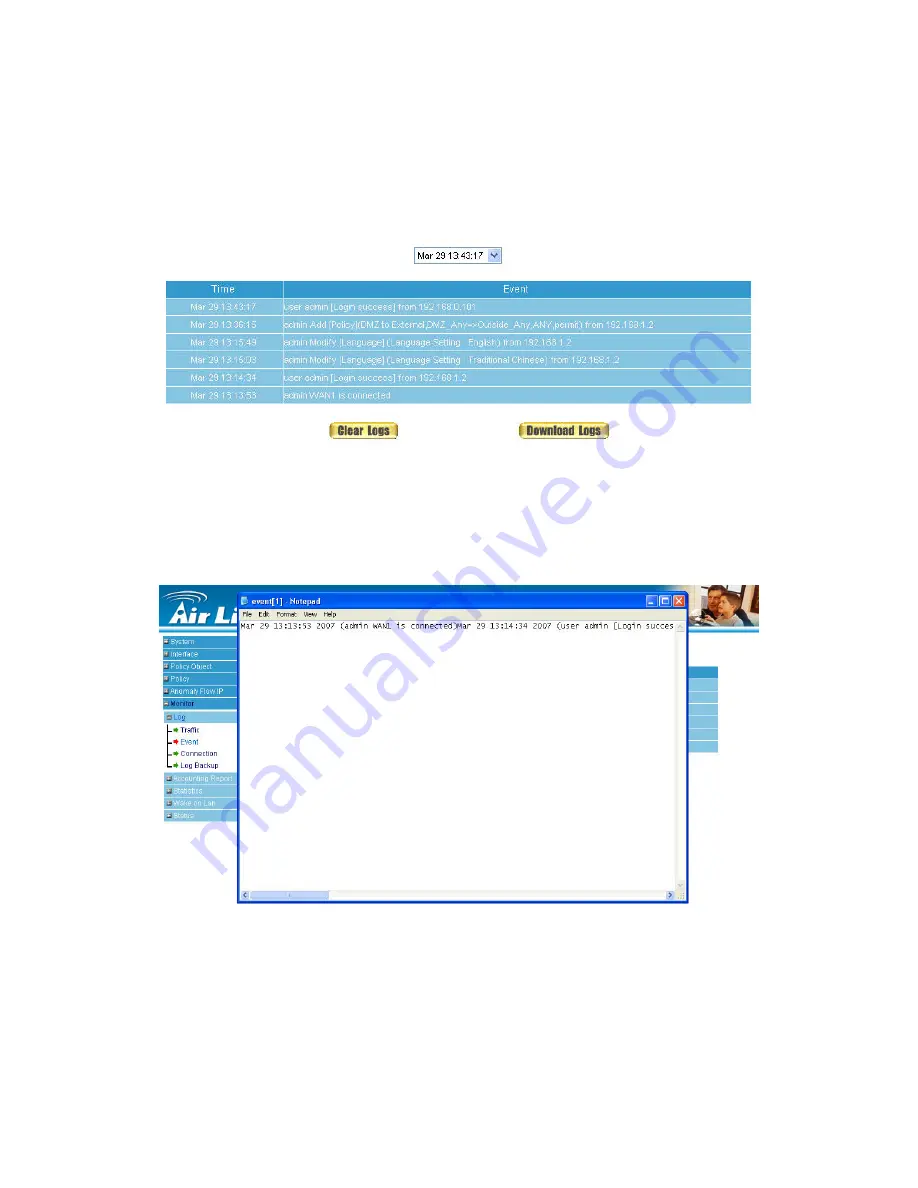
To record the detailed management events (such as Interface and event description of
RS-3000) of the Administrator
STEP 1
﹒
Click
Event
log of
LOG
. The management event records of the administrator will show up
(Figure21-6)
Figure21-6 Event Log WebUI
STEP 2
﹒
Click on
Download Logs
, RS-3000 will pop up a notepad file with the log recorded. User can
choose the place to save in PC instantly. (Figure21-7)
Figure21-7 Download Event Log Records WebUI
227
Summary of Contents for RS-3000
Page 1: ...1 RS 3000 Office UTM Gateway User s Manual ...
Page 45: ...Figure 5 11 PPTP Connection Figure 5 12 Complete PPTP Connection Setting 43 ...
Page 133: ...Figure15 3 Traffic Log Monitor WebUI 131 ...
Page 142: ...Figure15 19 Complete Policy Setting 140 ...
Page 183: ...Figure17 33 Create Folder WebUI 181 ...
Page 185: ...Figure17 35 Select Folder for Spam Mail to move to 183 ...
Page 187: ...Figure17 37 Compact SpamMail Folder 185 ...
Page 189: ...Figure17 39 Copy the File Address that SpamMail File Store 187 ...
Page 192: ...Figure17 42 Confirm that All of the Mail in SpamMail File had been Deleted 190 ...
Page 194: ...Figure17 44 Create Folder Function WebUI 192 ...
Page 196: ...Figure17 46 Select the Folder for Needed Spam Mail to Move to 194 ...
Page 198: ...Figure17 48 Compact HamMail File 196 ...
Page 200: ...Figure17 50 Copy the File Address that HamMail File Store 198 ...






























