22. Monitor
205
AirLive RS-2500 User’s Manual
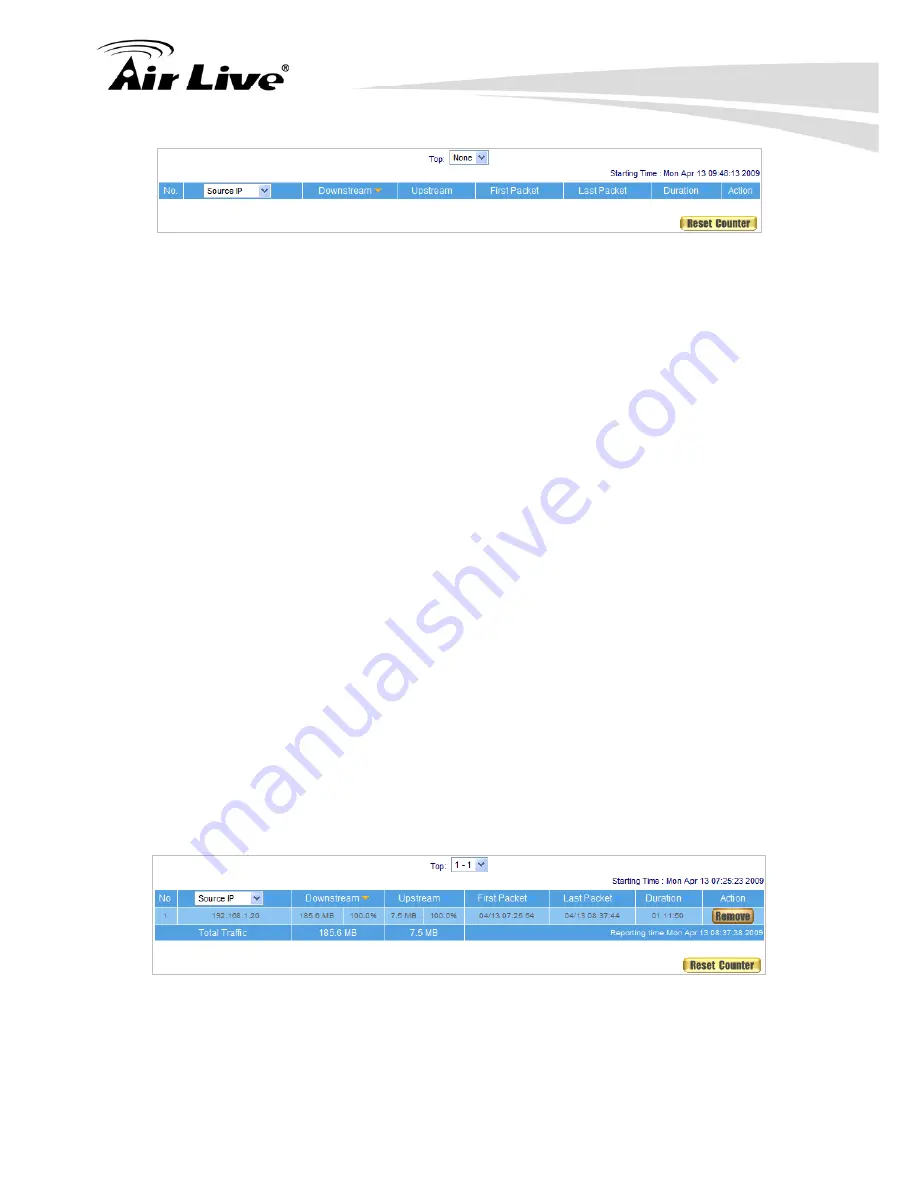
Figure 22-17 Outbound Source IP Statistics Report
STEP 3
﹒
Enter
Outbound
in
Accounting Report
and select
Destination IP
to inquire the
statistics of Send/Receive packets,
Downstream/Upstream, First packet/Last
packet/Duration
from the WAN Server to pass the RS-2500. (Figure 22-18)
TOP
:
Select the data you want to view; it presents 10 results in one page.
Destination IP
:
To display the report sorted by Destination IP, the IP address used
by WAN service serve
Downstream
:
The percentage of downstream and the value of each WAN service
hen the first packet is sent from WAN service server to LAN users,
n to refresh Accounting Report.
r connecting to RS-2500.
server which passes through RS-2500 to LAN user.
Upstream
:
The percentage of upstream and the value of each LAN user who passes
through RS-2500 to WAN service server.
First Packet
:
W
the sent time will be recorded by the RS-2500.
Last Packet
:
When the last packet from LAN user is sent to WAN service server, the
sent time will be recorded by the RS-2500.
Duration
:
The period of time between the first packet and the last packet.
Total Traffic
:
The RS-2500 will record and display the amount of Downstream and
Upstream packets passing from WAN Server to LAN user.
Reset Counter
:
Click Reset Counter butto
Figure 22-18 Outbound Destination IP Statistics Report
Summary of Contents for RS-2500
Page 1: ...User s Manual Dual WAN Security VPN Gateway RS 2500 ...
Page 218: ...22 Monitor 213 AirLive RS 2500 User s Manual Figure 22 23 To Detect WAN Statistics ...
Page 220: ...22 Monitor 215 AirLive RS 2500 User s Manual Figure 22 25 To Detect Policy Statistics ...
Page 224: ...22 Monitor 219 AirLive RS 2500 User s Manual Figure 22 30 Traceroute Results ...






























