Deploying the snom ONE IP Telephone System
74
The behavior of the access list is similar to a firewall. However, especially for TCP, a
firewall will keep the traffic completely out. Someone testing the system will not get a
response for a TCP request if the source IP address is not listed.
Example
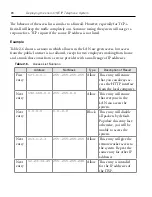
Table 2-6 shows a scenario in which all users in the LAN are given access, but access
from the public Internet is not allowed, except for two employees working from home
and a trunk that comes from a service provider with a small range of IP addresses.
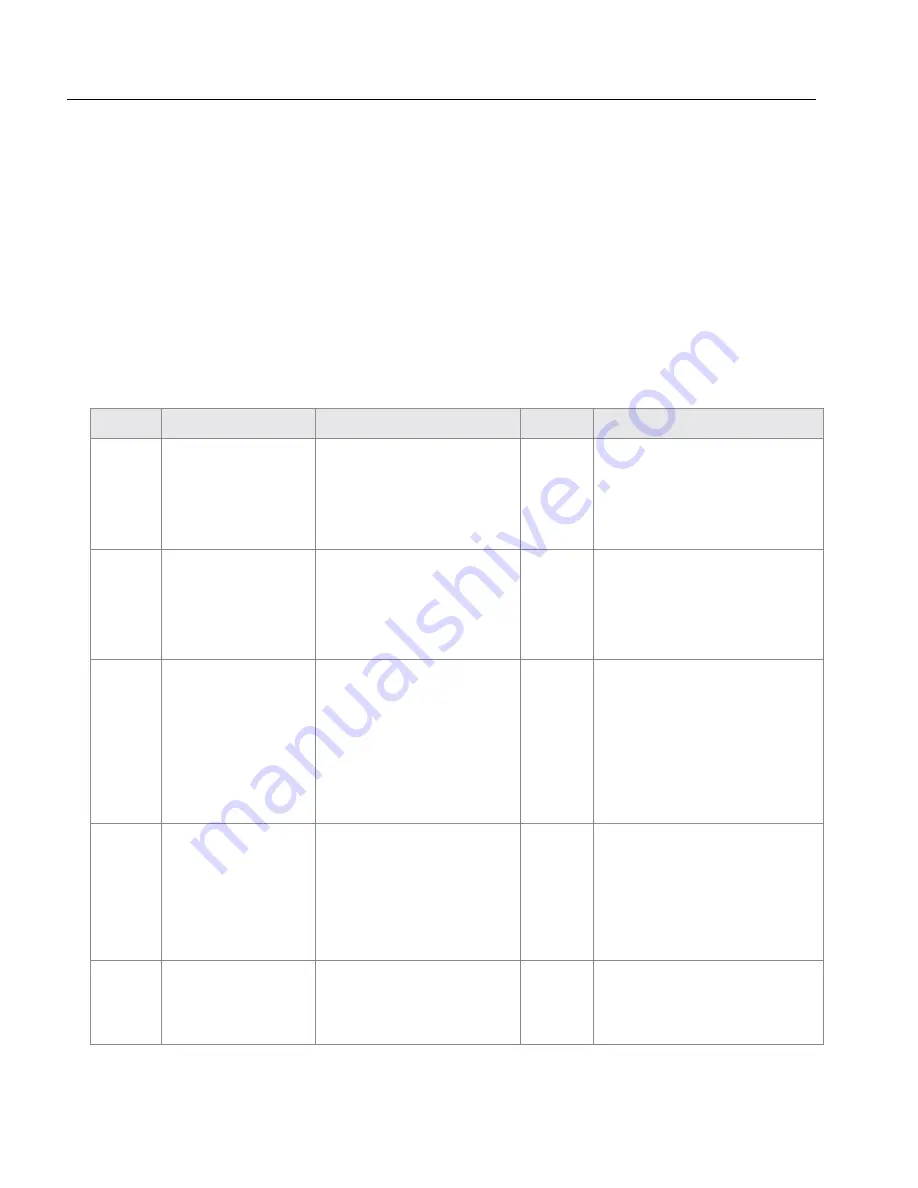
Table 2-6.
Access List Scenario
Address
Net Mask
Type
Description of Result
First
entry
127.0.0.1
255.255.255.255
Allow This entry will ensure
that you can always ac-
cess the HTTP interface
from the local computer.
Next
entry
192.168.0.0 255.255.0.0
Allow This entry will ensure
that everyone in the
LAN can access the
system.
Next
entry
0.0.0.0
0.0.0.0
Block This entry will disable
all packets by default.
Populate this entry last;
otherwise, you will be
unable to access the
system.
Next
entry
213.1.2.3
255.255.255.255
Allow This entry will give the
remote worker access to
the system. Repeat the
same entry for other IP
addresses.
Next
entry
12.23.34.45 255.255.255.248
Allow This entry is intended
for the IP addresses of
the ITSP.
Содержание ONE IP
Страница 4: ......
Страница 19: ...Part I Getting Started...
Страница 20: ...Part I Getting Started...
Страница 47: ...Part II Administering the System...
Страница 48: ...Part II Administering the System...
Страница 195: ...Deploying the snom ONE IP Telephone System 526...
Страница 201: ...Deploying the snom ONE IP Telephone System 532 Figure C 1 Trunk Settings for Configuration with Exchange 2007 2010 UM...
Страница 223: ......