Deploying the snom ONE IP Telephone System
72
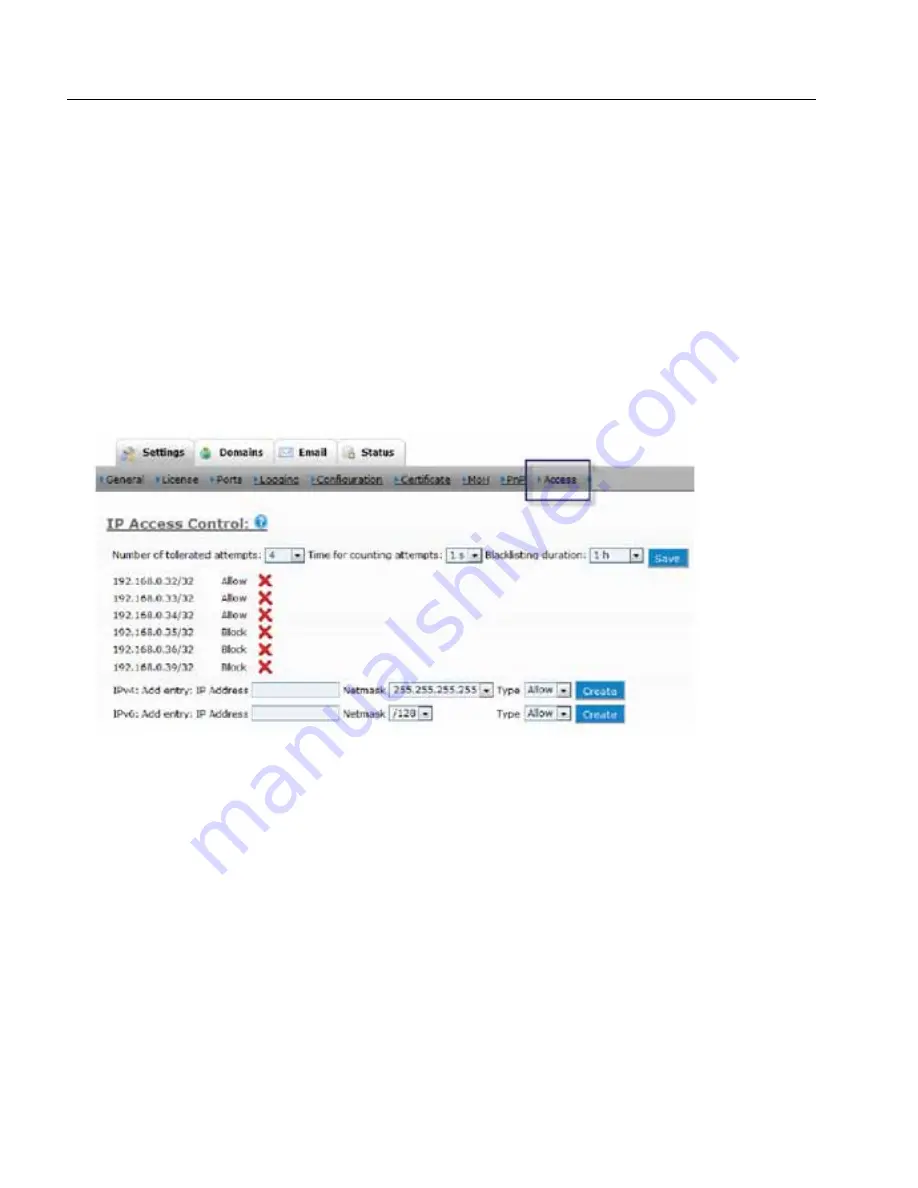
Access List
If your system is under a denial of service attack, the system will automatically block
the IP address that is attacking the system. You can also add IP addresses to the
Ac-
cess
page and place a
Block
on them so that they will be unable to access the system.
Just enter the IP address, the net mask, and the access type, and click
Create
. Enter
only as much information as needed by the net mask; for example, if the net mask is
“255.255.0.0,” enter
192.168.0.0
. To delete an entry, click the
Delete
button.
Changing the entry does not require a restart of the system. The changes take effect im-
mediately.
You may specify IP addresses with their netmask and their policy. If no match is found,
packets will be accepted. System administrators might want to define who has access to
the system for a number of reasons:
•
Protection against denial of service attacks: If you are operating the system on
publicly available addresses, there is always the risk that someone will try to
interrupt the service. Although the system has several protections against such
attacks, it might be easier to rule out such attacks from the beginning.
•
Limiting the service to authorized addresses: You might also want to limit the
service to specific IP addresses only. For example, while you might allow users
to register their IP phones in the office, you might allow only selected users
with their associated IP addresses to register their phones from home.
Содержание ONE IP
Страница 4: ......
Страница 19: ...Part I Getting Started...
Страница 20: ...Part I Getting Started...
Страница 47: ...Part II Administering the System...
Страница 48: ...Part II Administering the System...
Страница 195: ...Deploying the snom ONE IP Telephone System 526...
Страница 201: ...Deploying the snom ONE IP Telephone System 532 Figure C 1 Trunk Settings for Configuration with Exchange 2007 2010 UM...
Страница 223: ......