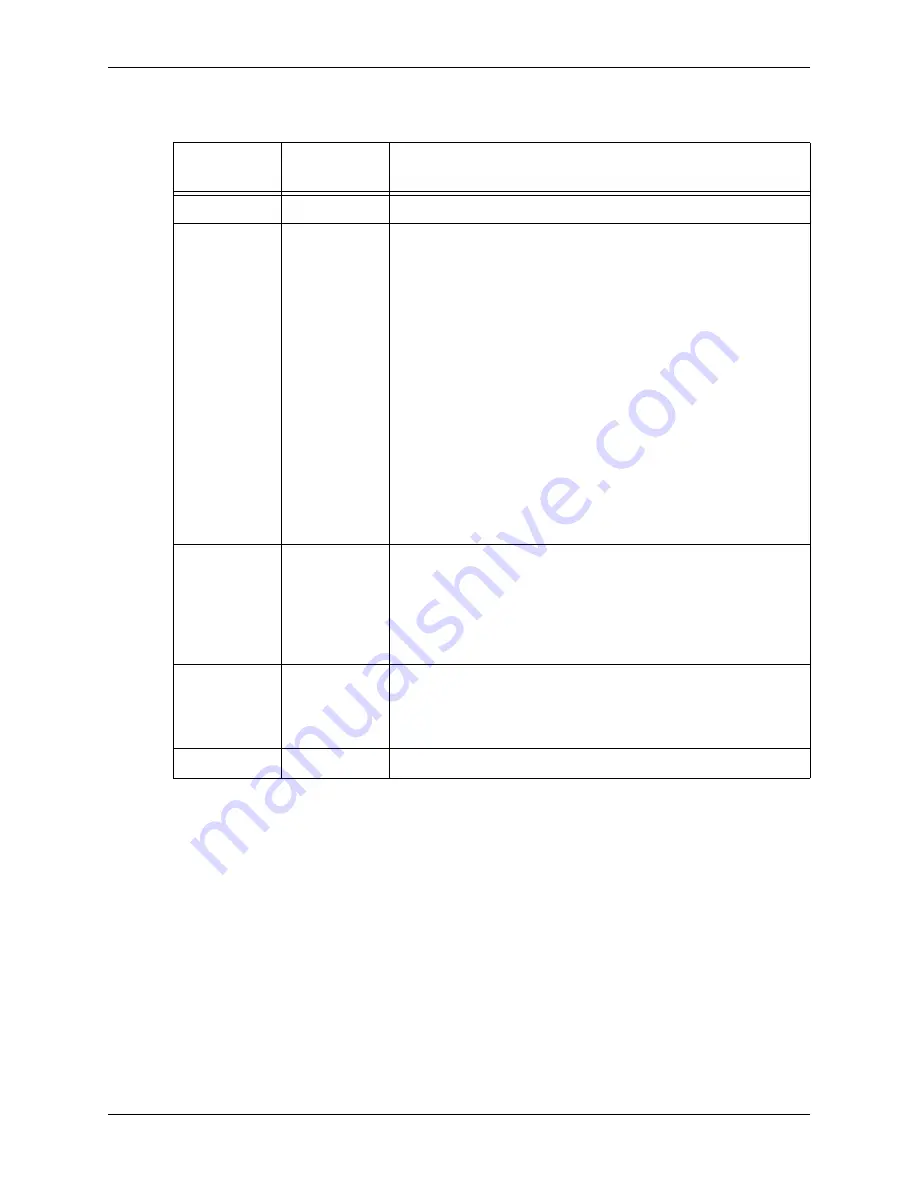
Threat Type
Selected
Column
Label
Description
Virus
Virus
Displays the type of virus detected in the email
Spam
Spam Score
Displays a score that indicates how likely that the email is spam.
•
A spam score of 90% - 98.9% is considered “medium”
likelihood if default settings are used.
•
A spam score of 99% or higher is considered “high” likelihood
if default settings are used.
Email Protection anti-spam filtering uses a large number of
filtering processes, as well as sophisticated statistical classification
techniques, as part of its Stacked Classification Framework® to
determine the score. If you specified an additional Realtime
Blackhole List (RBL) in the Anti-Spam window of the assigned
policy, the RBL can influence the spam score as well.
Note:
Occasionally, some emails might be marked as spam when in
fact they are legitimate emails. For these “false positive” email
messages, you can help Email Protection “tune” the spam
thresholds and rules by sending a forwarded copy of the email with
all content and attachments to [email protected].
Attachment
Attachment
Displays the name of an attachment that was included in the email
message and violates attachment rules (size, file typ, zip file
attachments) as defined on the Attachment windows of the
assigned policy. If a message contains more than one delinquent
attachment, the first attachment found in the message is listed. You
can check to see all attachments by opening the message.
Content
Keyword
Displays
Content
to indicate that the email that violated a content
policy, as defined in the Content Groups window for the assigned
policy. You can see what keywords were violated by opening the
message and checking the
Status
line.
All Threats
Type
Displays the type of threat filtering that the email violated.
Monitor Users’ Quarantined Email
Email Protectionr Administrator Guide
96
Proprietary: Not for use or disclosure outside McAfee without written permission.
November 2012
Sort the Search Results
You can sort the search results according to any of the columns in the Search Results
section.
1
Click on the heading of the column you want to sort.
You have the choice of sorting the messages in ascending or descending order of the
values in the column.
2
Click
Sort Ascending
or
Sort Descending
.






























