153
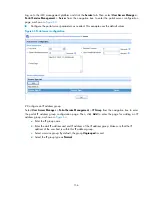
Figure 61
Configure cross-subnet portal authentication with extended functions
8.8.8.2/24
Router A
Host
GE1/0/2
20.20.20.1/24
Portal server
192.168.0.111/24
Radius server
192.168.0.112/24
GE1/0/1
192.168.0.100/24
Router B
GE1/0/2
8.8.8.1/24
GE1/0/1
20.20.20.2/24
Security policy server
192.168.0.113/24
Make sure that the IP address of the portal device added on the portal server is the IP address of the
interface connecting users (20.20.20.1, in this example) and that the IP address group associated with
the portal device is the network segment where the users reside (8.8.8.0/24, in this example).
Configure IP addresses for the host, routers, and servers as shown in
and make sure that
routes are available between devices.
Perform configurations on the RADIUS server to ensure that the user authentication and accounting
functions can work normally.
Configuration procedure
Configure Router A:
1.
Configure a RADIUS scheme.
# Create a RADIUS scheme named
rs1
and enter its view.
<RouterA> system-view
[RouterA] radius scheme rs1
# Set the server type for the RADIUS scheme. When using the iMC server, you must set the server type to
extended
.
[RouterA-radius-rs1] server-type extended
# Specify the primary authentication server and primary accounting server, and configure the keys for
communication with the servers.
[RouterA-radius-rs1] primary authentication 192.168.0.112
[RouterA-radius-rs1] primary accounting 192.168.0.112
[RouterA-radius-rs1] key authentication radius
[RouterA-radius-rs1] key accounting radius
[RouterA-radius-rs1] user-name-format without-domain
# Configure the IP address of the security policy server.
[RouterA-radius-rs1] security-policy-server 192.168.0.113
[RouterA-radius-rs1] quit