34-35
Cisco Catalyst Blade Switch 3120 for HP Software Configuration Guide
OL-12247-01
Chapter 34 Configuring Network Security with ACLs
Using VLAN Maps with Router ACLs
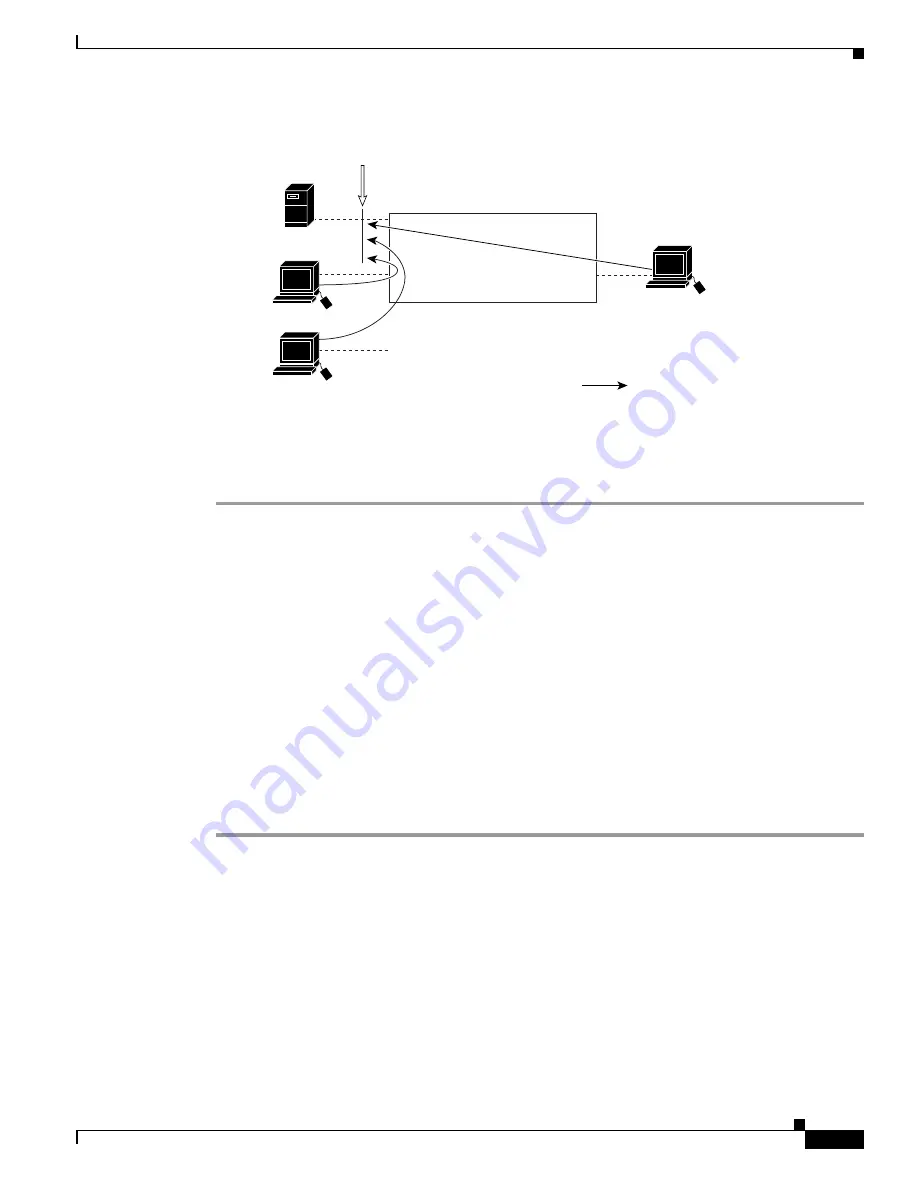
Figure 34-4
Deny Access to a Server on Another VLAN
This example shows how to deny access to a server on another VLAN by creating the VLAN map
SERVER 1 that denies access to hosts in subnet 10.1.2.0.8, host 10.1.1.4, and host 10.1.1.8 and permits
other IP traffic. The final step is to apply the map SERVER1 to VLAN 10.
Step 1
Define the IP ACL that will match the correct packets.
Switch(config)#
ip access-list extended SERVER1_ACL
Switch(config-ext-nacl))#
permit ip 10.1.2.0 0.0.0.255 host 10.1.1.100
Switch(config-ext-nacl))#
permit ip host 10.1.1.4 host 10.1.1.100
Switch(config-ext-nacl))#
permit ip host 10.1.1.8 host 10.1.1.100
Switch(config-ext-nacl))#
exit
Step 2
Define a VLAN map using this ACL that will drop IP packets that match SERVER1_ACL and forward
IP packets that do not match the ACL.
Switch(config)#
vlan access-map SERVER1_MAP
Switch(config-access-map)#
match ip address SERVER1_ACL
Switch(config-access-map)#
action drop
Switch(config)#
vlan access-map SERVER1_MAP 20
Switch(config-access-map)#
action forward
Switch(config-access-map)#
exit
Step 3
Apply the VLAN map to VLAN 10.
Switch(config)#
vlan filter SERVER1_MAP
vlan-list 10.
Using VLAN Maps with Router ACLs
To access control both bridged and routed traffic, you can use VLAN maps only or a combination of
router ACLs and VLAN maps. You can define router ACLs on both input and output routed VLAN
interfaces, and you can define a VLAN map to access control the bridged traffic.
If a packet flow matches a VLAN-map deny clause in the ACL, regardless of the router ACL
configuration, the packet flow is denied.
Layer 3 switch
Host (VLAN 20)
Host (VLAN 10)
Host (VLAN 10)
Server (VLAN 10)
101356
VLAN map
Subnet
10.1.2.0/8
10.1.1.100
10.1.1.4
10.1.1.8
Packet




































