31-12
Cisco Catalyst Blade Switch 3120 for HP Software Configuration Guide
OL-12247-01
Chapter 31 Configuring System Message Logging
Configuring System Message Logging
Beginning in privileged EXEC mode, follow these steps to enable configuration logging:
This example shows how to enable the configuration-change logger and to set the number of entries in
the log to 500.
Switch(config)#
archive
Switch(config-archive)#
log config
Switch(config-archive-log-cfg)#
logging enable
Switch(config-archive-log-cfg)#
logging size 500
Switch(config-archive-log-cfg)#
end
This is an example of output for the configuration log:
Switch#
show archive log config all
idx sess user@line Logged command
38 11 unknown user@vty3 |no aaa authorization config-commands
39 12 unknown user@vty3 |no aaa authorization network default group radius
40 12 unknown user@vty3 |no aaa accounting dot1x default start-stop group
radius
41 13 unknown user@vty3 |no aaa accounting system default
42 14 temi@vty4 |interface GigabitEthernet4/0/1
43 14 temi@vty4 | switchport mode trunk
44 14 temi@vty4 | exit
45 16 temi@vty5 |interface GigabitEthernet5/0/1
46 16 temi@vty5 | switchport mode trunk
47 16 temi@vty5 | exit
Configuring UNIX Syslog Servers
The next sections describe how to configure the UNIX server syslog daemon and how to define the UNIX
system logging facility.
Logging Messages to a UNIX Syslog Daemon
Before you can send system log messages to a UNIX syslog server, you must configure the syslog
daemon on a UNIX server. This procedure is optional.
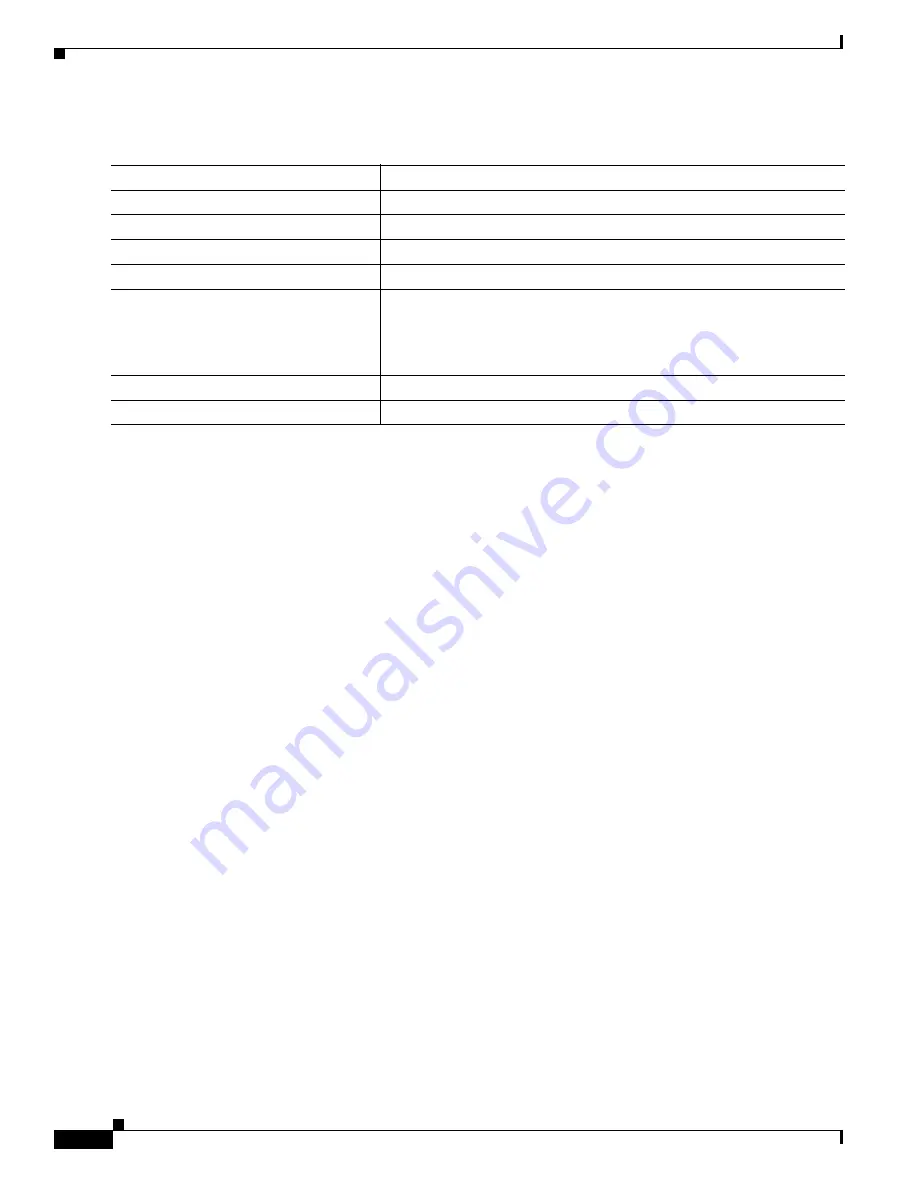
Command Purpose
Step 1
configure terminal
Enter global configuration mode.
Step 2
archive
Enter archive configuration mode.
Step 3
log config
Enter configuration-change logger configuration mode.
Step 4
logging enable
Enable configuration change logging.
Step 5
logging size entries
(Optional) Configure the number of entries retained in the configuration
log. The range is from 1 to 1000. The default is 100.
Note
When the configuration log is full, the oldest log entry is removed
each time a new entry is entered.
Step 6
end
Return to privileged EXEC mode.
Step 7
show archive log config
Verify your entries by viewing the configuration log.













































