Configuring GateLock
3
-
11
WARNING!
Passing an uncleaned virus to your computer puts your system at risk
and is not recommended.
• Click Delete if you want to remove the infected or malicious file from your
computer. Some malicious files, for example those infected by Trojans or
worms, cannot be cleaned and must therefore be deleted.
• Click Pass if you want GateLock to record the details of the infected or
malicious file in the antivirus log but do nothing to it.
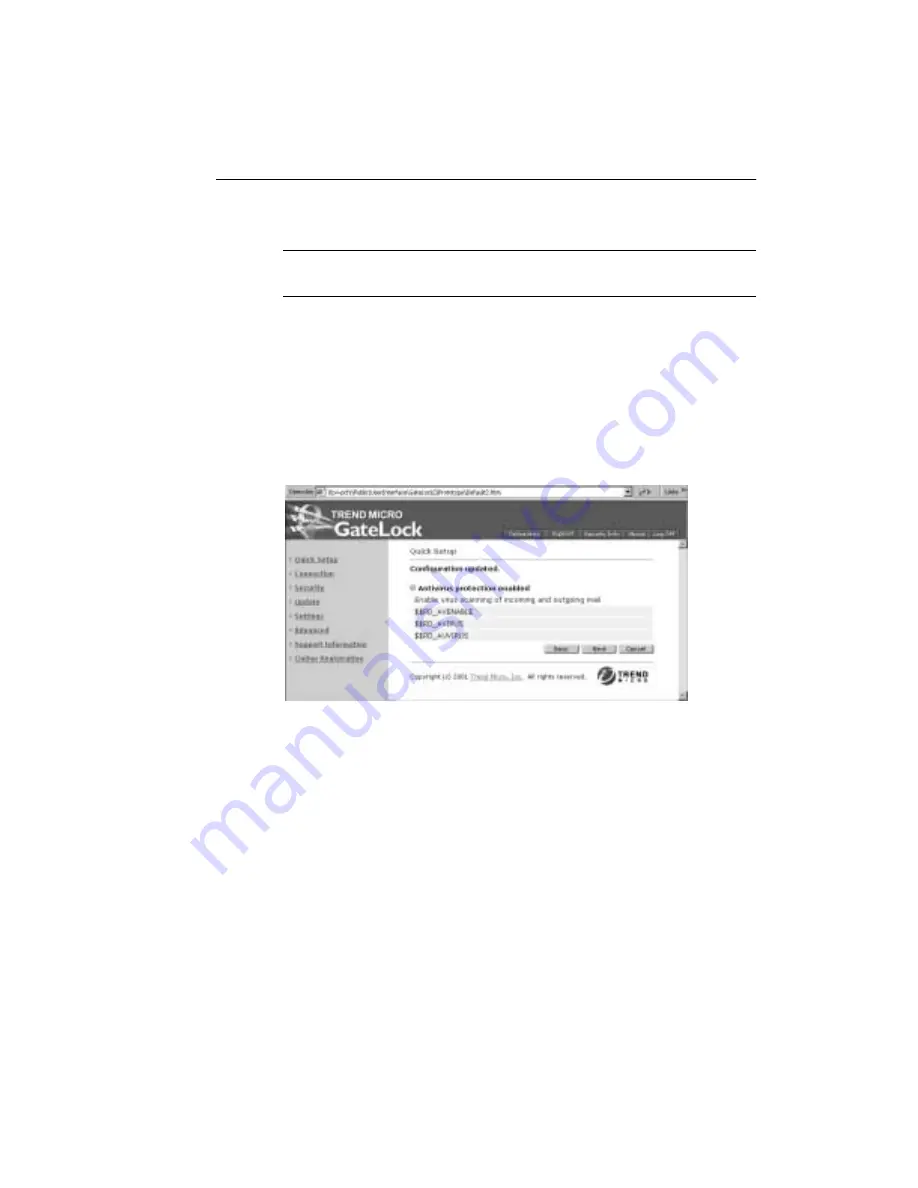
2. Click Next to save your antivirus protection settings. The information screen
shown in Figure 3-10. appears, displaying the settings you have just saved.
F
IGURE
3-10.
Antivirus Protection information screen
3. Click Next to advance to the Anti-Hacker Protection screen.
Anti-Hacker Protection
Another very important security feature of GateLock is anti-hacker protection. It can
protect your computer from hacker attacks with its built-in firewall and intrusion
detection features.
To protect your computer from unwanted intrusion, GateLock uses “port blocking.”
Think of a port as being similar to a door into your computer. Each service on the
Summary of Contents for GateLock
Page 1: ...Trend Micro GateLock Getting Started Guide...
Page 2: ......
Page 6: ...Trend Micro GateLock Getting Started Guide iv...
Page 16: ...Trend Micro GateLock Getting Started Guide 1 8...
Page 64: ...Trend Micro GateLock Getting Started Guide 4 8...
Page 78: ...Trend Micro GateLock Getting Started Guide A 14...
Page 85: ...ii Trend Micro GateLock Getting Started Guide...






























