Installing Cross-Pair Certificates
407
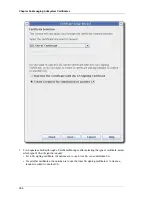
16.4.1. Installing Cross-Pair Certificates
Both cross-pair certificates can be imported into the Certificate System databases using the
certutil
tool or by selecting the
Cross-Pair Certificates
option from the Certificate Setup Wizard,
as described in
Section 16.5.1, “Installing Certificates in the Certificate System Database”
.
When both certificates have been imported into the database, a
crossCertificatePair
entry is
formed and stored in the database. The original individual cross-pair CA certificates are deleted once
the
crossCertificatePair
entry is created.
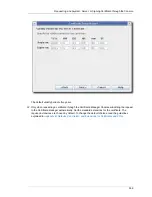
16.4.2. Searching for Cross-Pair Certificates
Both CAs in bridge certificates can store or publish the cross-pair certificates as a
crossCertificatePair
entry in an LDAP database. The Certificate Manager's internal database
can be searched for the
crossCertificatePair
entry with
ldapsearch
.
/usr/lib/mozldap/ldapsearch -D "cn=directory manager" -w secret -p 389 -h server.example.com -
b "o=server.example.com-pki-ca" -s sub "(crossCertificatePair=*)"
16.5. Managing the Certificate Database
Each Certificate System instance has a certificate database, which is maintained in its internal token.
This database contains certificates belonging to the subsystem installed in the Certificate System
instance and various CA certificates the subsystems use for validating the certificates they receive.
Even if an external token is used to generate and store key pairs, Certificate System always maintains
its list of trusted and untrusted CA certificates in its internal token.
This section explains how to view the contents of the certificate database, delete unwanted
certificates, and change the trust settings of CA certificates installed in the database using the
Certificate System window. For information on adding certificates to the database, see
Section 16.5.1,
“Installing Certificates in the Certificate System Database”
.
NOTE
The Certificate System command-line utility
certutil
can be used to manage the
certificate database by editing trust settings and adding and deleting certificates. For
details about this tool, see
http://www.mozilla.org/projects/security/pki/nss/tools/
.
Administrators should periodically check the contents of the certificate database to make sure that it
does not include any unwanted CA certificates. For example, if the database includes CA certificates
that should not ever be trusted within the PKI setup, delete them.
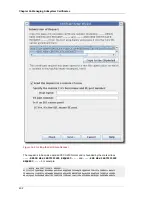
16.5.1. Installing Certificates in the Certificate System Database
If new server certificates are issued for a subsystem, they must be installed in that subsystem
database. Additionally, user and agent certificates must be installed in the subsystem databases. If the
certificates are issued by an external CA, then usually the corresponding CA certificate or certificate
chain needs to be installed.
Certificates can be installed in the subsystem certificate database through the Console's Certificate
Setup Wizard or using the
certutil
utility.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...