Chapter 16. Managing Subsystem Certificates
394
When an HSM is used to store certificates, then the HSM name is prepended to the certificate
nickname, and the full name is used in the subsystem configuration, such as the
server.xml
file. For
example:
serverCert="nethsm:Server-Cert cert-pki-ca
instanceID
NOTE
A single HSM can be used to store certificates and keys for mulitple subsystem instances,
which may be installed on multiple hosts. When an HSM is used, any certificate nickname
for a subsystem must be unique for every subsystem instance managed on the HSM.
Certificate System supports two types of HSM, nCiphers netHSM 2000 and Chrysalis LunaSA.
16.2. Requesting a Subsystem, Server, or Signing
Certificate through the Console
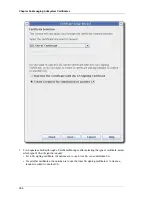
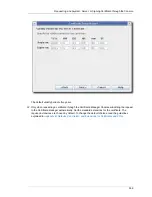
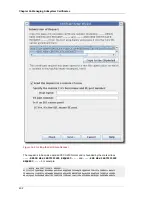
The Certificate Setup Wizard for the CA, OCSP, DRM, and TKS automates the certificate enrollment
process for subsystem certificates. The Console can create, submit, and install certificate requests
and certificates for any of the certificates used by that subsystem. These certificates can be a
server certificate or subsystem-specific certificate, such as a CA signing certificate or DRM transport
certificate.
NOTE
It is important that the agent or user generate and submit the client request from the
computer that will be used later to access the subsystem because part of the request
process generates a private key on the local machine. If location independence is
required, the user can also use a hardware token, such as a smart card, to store the key
pair and the certificate.
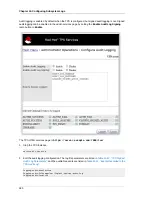
To create a certificate request using the subsystem administrative console:
1. Open the subsystem console.
pkiconsole https://server.example.com:9445/ca
2. In the
Configuration
tab, select
System Keys and Certificates
in the navigation tree.
3. In the right panel, select the
Local Certificates
tab.
4. Click
Add/Renew
.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...