Changing the Trust Settings of a CA Certificate
413
/var/lib/
subsystem_name
/alias
2. List the certificates in the database by running the
certutil
with the
-L
option. For example:
certutil -L -d .
Certificate Authority - Example Domain CT,c,
subsystemCert cert-subsystem u,u,u
Server-Cert cert-example u,u,u
3. Delete the certificate by running the
certutil
with the
-D
option.
certutil -D -d . -n
certificate_nickname
For example:
certutil -D -d . -n "ServerCert cert-example"
4. List the certificates again to confirm that the certificate was removed.
certutil -L -d .
Certificate Authority - Example Domain CT,c,
subsystemCert cert-subsystem u,u,u
For information about using the
certutil
command, see
http://www.mozilla.org/projects/security/pki/
nss/tools/certutil.html
.
16.6. Changing the Trust Settings of a CA Certificate
Certificate System subsystems use the CA certificates in their certificate databases to validate
certificates received during an SSL-enabled communication.
It can be necessary to change the trust settings on a CA stored in the certificate database, temporarily
or permanently. For example, if there is a problem with access or compromised certificates, marking
the CA certificate as untrusted prevents entities with certificates signed by that CA from authenticating
to the Certificate System. When the problem is resolved, the CA can be marked as trusted again.
To untrust a CA permanently, consider removing its certificate from the trust database. For
instructions, see
Section 16.5.3, “Deleting Certificates from the Database”
.
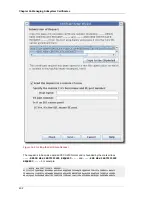
16.6.1. Changing Trust Settings through the Console
To change the trust setting of a CA certificate, do the following:
1. Open the subsystem console.
pkiconsole https://server.example.com:
admin_port/subsystem_type
2. In the
Configuration
tab,
System Keys and Certificates
from the left navigation tree.
3. Select the
CA certificates
tab.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...