Requiring System Password Prompts
287
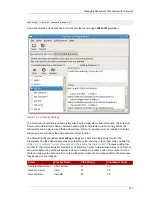
service pki-ca start
b. Monitor the Tomcat web server log file,
catalina.out
, and the debug log. For example:
tail -f /var/log/pki-ca/catalina.out /var/log/pki-ca/debug
The server process will hang as it restarts because it is waiting for the input from the default
password.conf
file.
c. Redirect the password to the
password.conf
pipe. Assuming that the backup file for
password.conf
is called
password.bak
, run
cat password.bak > password.conf
.
Repeat this command until the server is fully started; this is apparent in the debug log.
This process still uses a clear text password file,
password.bak
, but this moves the password store
so that it is external to the Certificate System instance and can be stored anywhere, such as a smart
card. This only requires a utility which can reconstruct the original password file. For example, this
processes uses the
zip
tool to protect the password file:
1. Zip and protect the
password.conf
file using
zip
.
zip -e secret.zip password.conf
2. Delete the
password.conf
file, and create a pipe called
password.conf
.
3. Run the regular start script.
4. Monitor the Tomcat web server log,
catalina.out
, and the debug log.
5. Provide the passwords to the subsystem instance by running the following:
unzip -c secret.zip password.conf > password.conf
This is a simple and very flexible way to protect the clear text password file while still allowing
passwords to be managed easily through a text editor.
12.3.3. Requiring System Password Prompts
The
password.conf
file stores system passwords in plaintext. Although the procedures in
Section 12.3.2, “Protecting the password.conf File”
offers some security for the stored passwords,
some administrators prefer to enter system passwords manually and to remove the password file
entirely.
When a Certificate System instance starts, the subsystem automatically checks for the
password.conf
file. If the file exists, then it uses those passwords to connect to other services, like
the internal LDAP database. If that file does not exist, then the subsystem instance starts a watchdog
daemon to start and stop the subsystem process and to send the subsystem passwords to other
services. The watchdog prompts for all of the passwords required by the subsystem.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...