Chapter 2. Making Rules for Issuing Certificates
38
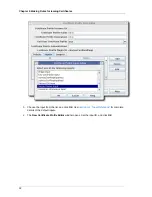
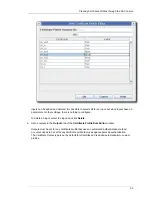
2.2.3.2. Modifying Certificate Extensions through the Command Line
Changing constraints changes the restrictions on the type of information which can be supplied.
Changing the defaults and constraints can also add, delete, or modify the extensions which are
accepted or required from a certificate request.
For example, the default caFullCMCUserCert profile is set to create a Key Usage extension from
information in the request.
policyset.cmcUserCertSet.6.constraint.class_id=keyUsageExtConstraintImpl
policyset.cmcUserCertSet.6.constraint.name=Key Usage Extension Constraint
policyset.cmcUserCertSet.6.constraint.params.keyUsageCritical=true
policyset.cmcUserCertSet.6.constraint.params.keyUsageCrlSign=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageDataEncipherment=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageDecipherOnly=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageDigitalSignature=true
policyset.cmcUserCertSet.6.constraint.params.keyUsageEncipherOnly=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageKeyAgreement=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageKeyCertSign=false
policyset.cmcUserCertSet.6.constraint.params.keyUsageKeyEncipherment=true
policyset.cmcUserCertSet.6.constraint.params.keyUsageNonRepudiation=true
policyset.cmcUserCertSet.6.default.class_id=keyUsageExtDefaultImpl
policyset.cmcUserCertSet.6.default.name=Key Usage Default
policyset.cmcUserCertSet.6.default.params.keyUsageCritical=true
policyset.cmcUserCertSet.6.default.params.keyUsageCrlSign=false
policyset.cmcUserCertSet.6.default.params.keyUsageDataEncipherment=false
policyset.cmcUserCertSet.6.default.params.keyUsageDecipherOnly=false
policyset.cmcUserCertSet.6.default.params.keyUsageDigitalSignature=true
policyset.cmcUserCertSet.6.default.params.keyUsageEncipherOnly=false
policyset.cmcUserCertSet.6.default.params.keyUsageKeyAgreement=false
policyset.cmcUserCertSet.6.default.params.keyUsageKeyCertSign=false
policyset.cmcUserCertSet.6.default.params.keyUsageKeyEncipherment=true
policyset.cmcUserCertSet.6.default.params.keyUsageNonRepudiation=true
This extension can be removed so that the server accepts the key usage set in the request. In this
example, the key extension constraint is removed and replaced by no constraint, and the default is
updated to allow user-supplied key extensions:
policyset.cmcUserCertSet.6.constraint.class_id=noConstraintImpl
policyset.cmcUserCertSet.6.constraint.name=No Constraint to keep it simple
policyset.cmcUserCertSet.6.default.class_id=userExtensionDefaultImpl
policyset.cmcUserCertSet.6.default.name=User Supplied Key Default
policyset.cmcUserCertSet.6.default.params.userExtOID=2.5.29.15
This sets the server to accept the extension OID
2.5.29.15
in the certificate request.
NOTE
If the User Supplied Extension Default is used, the CA expects any extensions which are
specified with the specified userExtOID parameters in the request.
Other constraints and defaults can be changed similarly. Make sure that any required constraints and
included with the appropriate default, that defaults are changed when a different constraint is required,
and that only allowed constraints are used with the default. For more information, see
Section B.1,
“Defaults Reference”
and
Section B.2, “Constraints Reference”
.
Summary of Contents for CERTIFICATE SYSTEM 8.0 - ADMINISTRATION
Page 42: ...20 ...
Page 43: ...Part I Setting up Certificate Services ...
Page 44: ......
Page 190: ...168 ...
Page 208: ...186 ...
Page 223: ...Part II Additional Configuration to Manage CA Services ...
Page 224: ......
Page 256: ...234 ...
Page 270: ...248 ...
Page 280: ...258 ...
Page 292: ...270 ...
Page 293: ...Part III Managing the Subsystem Instances ...
Page 294: ......
Page 408: ...386 ...
Page 438: ...416 ...
Page 439: ...Part IV References ...
Page 440: ......
Page 503: ...Netscape Defined Certificate Extensions Reference 481 OID 2 16 840 1 113730 13 ...
Page 504: ...482 ...
Page 556: ...534 ...
Page 564: ...542 ...