Chapter 2: Configuring System Information
|
53
FS728TP Smart Switch Software Administration Manual
SNMP
From SNMP link under the System tab, you can configure SNMP settings for SNMP V1/V2
and SNMPv3.
From the SNMP link, you can access the following pages:
•
SNMPV1/V2
on page
53
•
Trap Flags
on page
55
•
SNMP v3 User Configuration
on page
57
SNMPV1/V2
The pages under the SNMPV1/V2 menu allow you to configure SNMP community
information, traps, and trap flags.
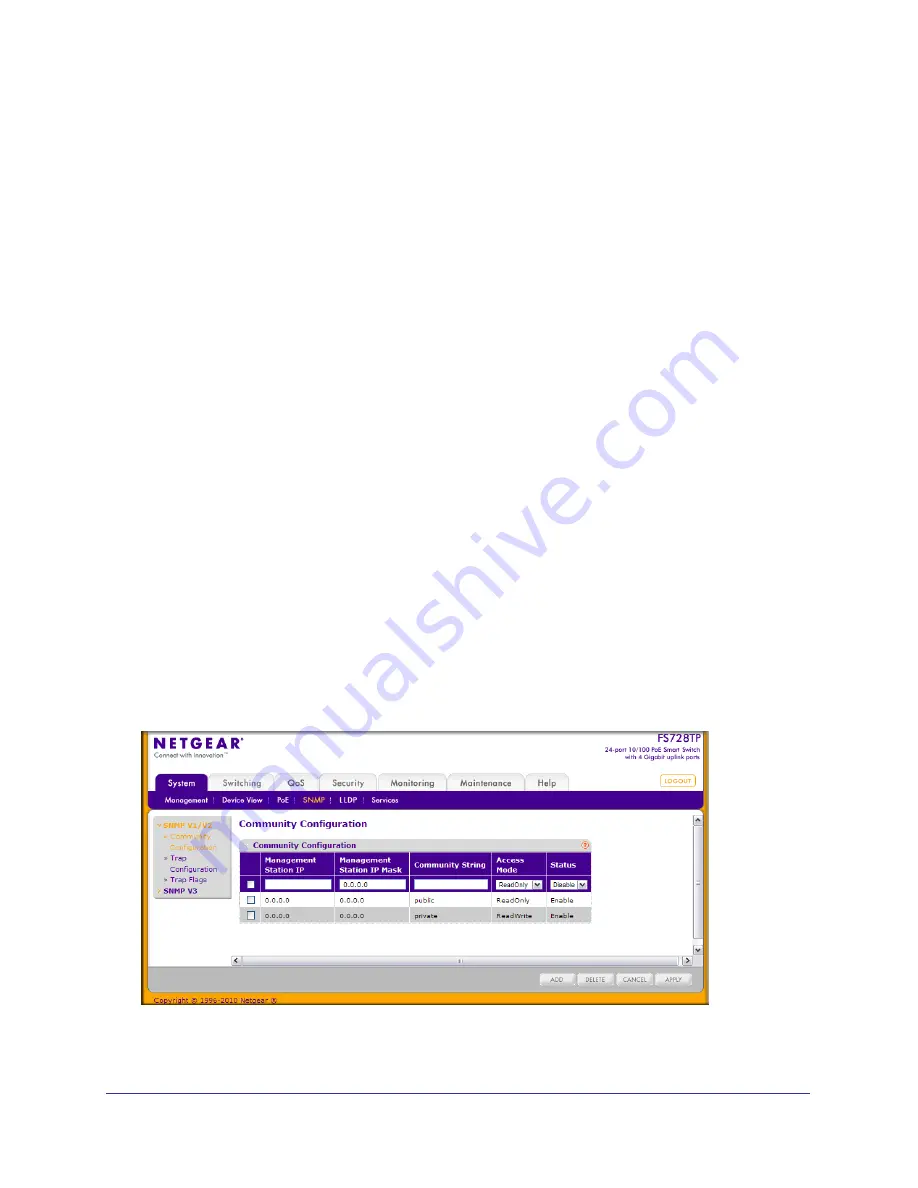
Community Configuration
To display this page, click
System
SNMP
SNMP V1/V2
Community Configuration
.
By default, two SNMP Communities exist:
•
Private, with Read/Write privileges and status set to
Enable
.
•
Public, with Read Only privileges and status set to
Enable
.
These are well-known communities. Use this page to change the defaults or to add other
communities. Only the communities that you define using this page will have access to the
switch using the SNMPv1 and SNMPv2c protocols. Only those communities with read/write
level access can be used to change the configuration using SNMP.
Use this page when you are using the SNMPv1 and SNMPv2c protocol.
Summary of Contents for FS728TP - ProSafe 24 Port 10/100 Smart Switch
Page 8: ...FS728TP Smart Switch Software Administration Manual 8 Table of Contents ...
Page 188: ...188 Chapter 5 Managing Device Security FS728TP Smart Switch Software Administration Manual ...
Page 231: ...Chapter 8 Help 231 FS728TP Smart Switch Software Administration Manual ...
Page 261: ...Index 261 FS728TP Smart Switch Software Administration Manual ...






























