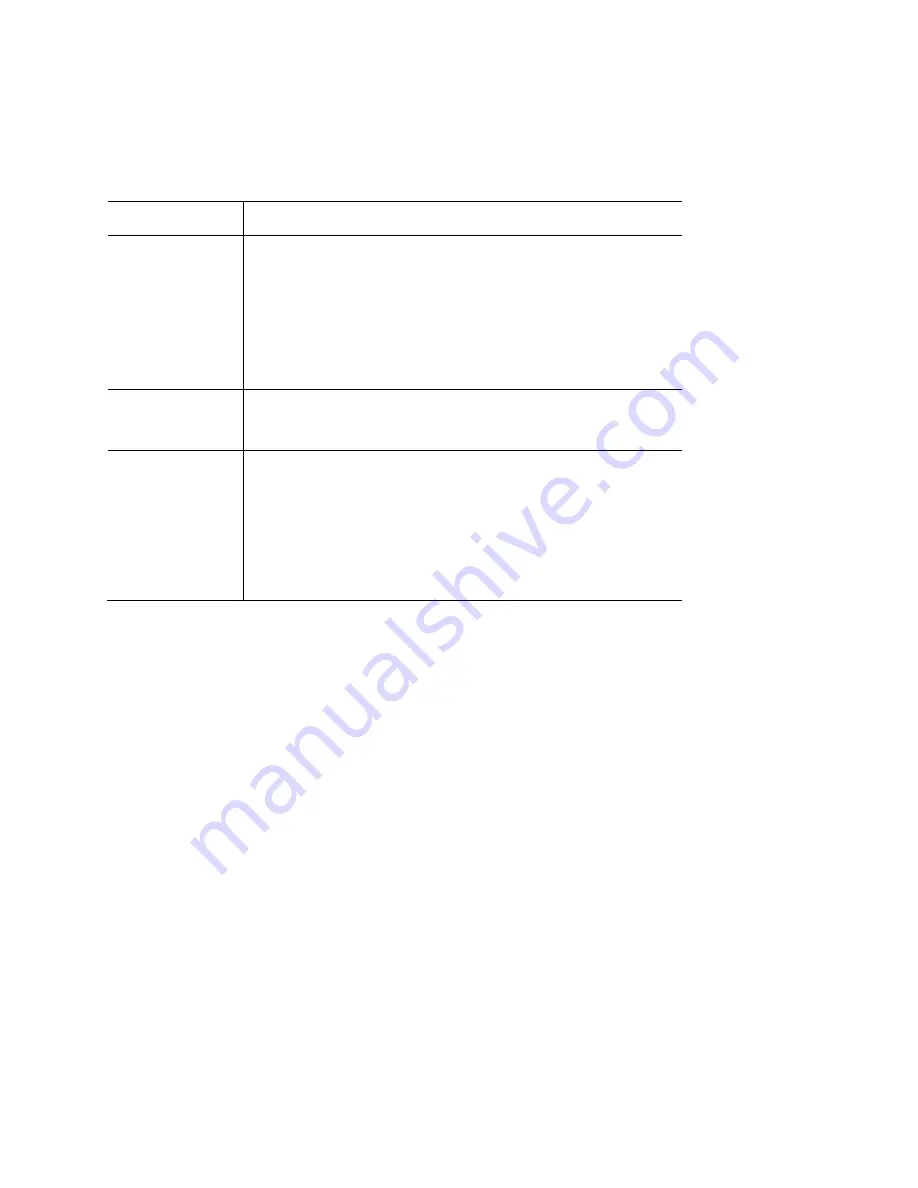
Wireless Station Configuration
For each of the following, wireless stations must have the same settings as the wireless access
point.
Mode
On each PC, the mode must be set to Infrastructure.
SSID (ESSID)
This must match the value used on the wireless access
point.
The default value is LinksysSMB24Gfor radio 1 and
LinksysSMB5Gfor radio 2
.
Note—The SSID is case sensitive.
802.1x
Authentication
Each client must obtain a certificate for authentication for
the RADIUS server.
802.1x
Encryption
Typically, EAP-TLS is used. This is a dynamic key system,
so keys do NOT have to be entered on each wireless
station.
You can also use a static WEP key (EAP-MD5). The
wireless access point supports both methods
simultaneously.
RADIUS Server Configuration
If using WPA2-Enterprise mode, the RADIUS server on your network must be configured as
follows:
•
It must provide and accept certificates for user authentication.
•
There must be a client login for the wireless access point itself.
•
The wireless access point will use its default name as its client login name. (However, your
RADIUS server may ignore this and use the IP address instead.)
•
The Shared Key, set on the Security screen of the access point, must match the Shared
Secret value on the RADIUS server.
•
Encryption settings must be correct.
121
Summary of Contents for LAPAC2600
Page 1: ...User Guide AC2600 Dual Band Wireless Access Point LAPAC2600 1 ...
Page 86: ...Master 86 ...
Page 94: ...Buttons Refresh Click to update the data on the screen 94 ...
Page 131: ...12 Select No if you don t want to view the help for EAP Click Finish 131 ...
Page 138: ...Setup for Windows XP and 802 1x client is now complete 138 ...
Page 140: ...LNKPG 00333 Rev A00 140 ...
















































