252
Protection modes
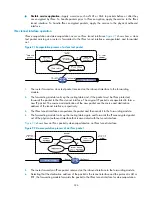
Data flows can be protected in the following modes:
•
Standard mode
—One tunnel protects one data flow. The data flow permitted by an ACL rule is
protected by one tunnel that is established solely for it.
•
Aggregation mode
—One tunnel protects all data flows permitted by all the rules of an ACL. This
mode applies to only scenarios where one end runs Comware V3, the other end runs Comware
V5, and IKE is used for negotiation.
NOTE:
•
For more information about ACL configuration, see
ACL and QoS Configuration Guide.
•
To use IPsec in combination with QoS, make sure that IPsec's ACL classification rules match the QoS
classification rules. If the rules do not match, QoS may assign the packets of one IPsec SA to different
queues, causing packets to be sent out of order. When the anti-replay function is enabled, IPsec
discards the packets beyond the anti-replay window in the inbound direction, resulting in packet loss.
For more information, see
ACL and QoS Configuration Guide.
Configuring an IPsec proposal
An IPsec proposal, part of an IPsec policy or an IPsec profile, defines the security parameters for IPsec
SA negotiation, including the security protocol, encryption/authentication algorithms, and encapsulation
mode.
To configure an IPsec proposal:
To do…
Command…
Remarks
1.
Enter system view.
system-view
—
2.
Create an IPsec proposal and
enter its view.
ipsec
proposal
proposal-
name
Required.
By default, no IPsec proposal exists.
3.
Specify the security protocol for
the proposal.
transform
{
ah
|
ah-esp
|
esp
}
Optional.
ESP by default.
4.
Specify the
security
algorithms.
Specify the
encryption algorithm
for ESP.
esp
encryption-algorithm
{
3des
|
aes
[
key-length
] |
des
}
Optional.
DES by default.
Specify the
authentication
algorithm for ESP.
esp
authentication-
algorithm
{
md5
|
sha1
}
Optional.
MD5 by default.
Specify the
authentication
algorithm for AH.
ah
authentication-
algorithm
{
md5
|
sha1
}
Optional.
MD5 by default.