150
4.
Configure extended portal authentication.
# Configure the portal server as needed:
[Router] portal server newpt ip 192.168.0.111 key portal port 50100 url
http://192.168.0.111:8080/portal
# Enable extended portal authentication on the interface connecting the host.
[Router] interface gigabitethernet 1/0/2
[Router–Gigabitethernet1/0/2] portal server newpt method direct
[Router–Gigabitethernet1/0/2] quit
Configuring re-DHCP portal authentication with extended
functions
Network requirements
As shown in
:
•
The host is directly connected to the router, and the router is configured for re-DHCP extended
portal authentication. The host is assigned with an IP address through the DHCP server. Before
extended portal authentication, the host uses an assigned private IP address. After passing the
authentication, the host can obtain a public IP address.
•
If a user fails security check after passing identity authentication, the user can access only subnet
192.168.0.0/24. After passing security check, the user can access Internet resources.
•
A RADIUS server serves as the authentication/accounting server.
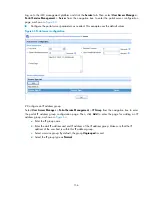
Figure 60
Configure re-DHCP portal authentication with extended functions
192.168.0.111/24
192.168.0.114/24
192.168.0.112/24
Router
Host
automatically obtains
an IP address
GE1/0/2
20.20.20.1/24
10.0.0.1/24 sub
GE1/0/1
192.168.0.100/24
Portal server
Security policy server
DHCP server
192.168.0.113/24
RADIUS server
For re-DHCP authentication, you must configure a public address pool (20.20.20.0/24, in this example)
and a private address pool (10.0.0.0/24, in this example) on the DHCP server. The configuration steps
are omitted.
For re-DHCP authentication, the router must be configured as a DHCP relay agent (instead of a DHCP
server) and the portal-enabled interface must be configured with a primary IP address (a public IP
address) and a secondary IP address (a private IP address). For information about DHCP relay agent
configuration, see
Layer 3—IP Services Configuration Guide
.