240
Configuring a certificate attribute-based access control policy
Network requirements
•
The client accesses the remote HTTPS server through the HTTPS protocol.
•
Configure SSL to ensure that only legal clients log into the HTTPS server.
•
Create a certificate attribute-based access control policy to control access to the HTTPS server.
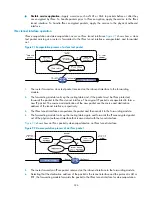
Figure 89
Configure a certificate attribute-based access control policy
CA server
IP network
Host
Router
HTTPS client
HTTPS server
For more information about SSL configuration, see "
For more information about HTTPS configuration, see
Fundamentals Configuration Guide
.
The PKI domain to be referenced by the SSL policy must be created in advance. For information about
how to configure a PKI domain, see "
."
Configuration procedure
1.
Configure the HTTPS server.
# Configure the SSL policy for the HTTPS server to use.
<Router> system-view
[Router] ssl server-policy myssl
[Router-ssl-server-policy-myssl] pki-domain 1
[Router-ssl-server-policy-myssl] client-verify enable
[Router-ssl-server-policy-myssl] quit
2.
Configure the certificate attribute group.
# Create certificate attribute group
mygroup1
and add two attribute rules. The first rule defines that the
DN of the subject name includes the string
aabbcc
, and the second rule defines that the IP address of the
certificate issuer is 10.0.0.1.
[Router] pki certificate attribute-group mygroup1
[Router-pki-cert-attribute-group-mygroup1] attribute 1 subject-name dn ctn aabbcc
[Router-pki-cert-attribute-group-mygroup1] attribute 2 issuer-name ip equ 10.0.0.1
[Router-pki-cert-attribute-group-mygroup1] quit