95
Countermeasure:
Configure
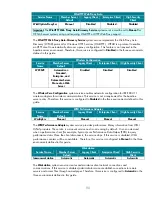
MSS: Syn attack protection level (protects against DoS)
to a value of
Connections time out sooner if a SYN attack is detected.
The possible values for this Registry value
are:
•
1
or
0
; default is
0
(disabled)
In the SCE UI, these options appear as:
•
Connections time-out more quickly if a SYN attack is detected
•
No additional protection, use default settings
•
Not Defined
Potential Impact:
This value adds additional delays to connection indications, and TCP connection
requests quickly time-out when a SYN attack is in progress. Configuring this setting causes the
scalable windows and TCP parameters that are configured on each adapter-including Initial Round
Trip Time (RTT) and window size socket options no longer work.
EnableDeadGWDetect: Allow automatic detection of dead network
gateways (could lead to DoS)
This entry appears as
MSS: Allow automatic detection of dead network gateways (could lead to DoS)
in the SCE. When dead-gateway detection is enabled, TCP may ask the IP to change to a backup
gateway if a number of connections are experiencing difficulty.
Vulnerability:
An attacker could force the server to switch gateways, potentially to an unintended
one.
Countermeasure:
Configure
MSS: Allow automatic detection of dead network gateways (could
lead to DoS)
to a value of
Disabled
. The possible values for this Registry value are:
•
1
or
0
; default is
0
(disabled)
In the SCE UI, these options appear as:
•
Enabled
•
Disabled
•
Not Defined
Potential Impact:
Configuring this setting to 0 prevents Windows from detecting dead gateways
and automatically switching to an alternate.
EnablePMTUDiscovery: Allow automatic detection of MTU size (possible
DoS by an attacker using a small MTU)
This entry appears as
MSS: Allow automatic detection of MTU size (possible DoS by an attacker using
a small MTU)
in the SCE. When this value is enabled, the default setting, the TCP stack tries to
automatically determine either the maximum transmission unit (MTU) or the largest packet size over
the path to a remote host.
Vulnerability:
If administrators do not set this value to 0, an attacker could force the MTU to a very
small value and overwork the stack by forcing the server to fragment a large number of packets.
Countermeasure:
Configure
MSS: Allow automatic detection of MTU size (possible DoS by an
attacker using a small MTU)
to a value of
Disabled
. The possible values for this Registry value are: