134
Important:
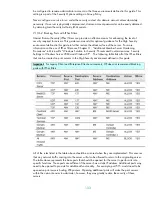
These changes could affect performance and should be tested prior to implementing in
production. The exact number of ports that will be opened will depend on the environment as well as
the use and functionality of the server. If print server performance or responsiveness degrades,
additional ports may need to be opened.
Because of the large amount of interaction between a domain member and the domain controller, in
particular RPC and authentication traffic, all communications are permitted between a print server and
all domain controllers. Traffic could be further limited, but most environments would require the
creation of dozens of additional filters in order for the filters to effectively protect the server. This
would make it very difficult to implement and manage IPSec policies. Similar rules should be created
for each of the domain controllers a print server will interact with. To increase the reliability and
availability of print servers, this will often include adding rules for all domain controllers in the
environment.
As seen above, if Microsoft Operations Manager (MOM) is implemented in the environment, all
network traffic must be allowed to travel between the server where the IPSec filters are implemented
and the MOM server. This is necessary because of the large amount of interaction between the MOM
server and the OnePoint client-the client application that reports to the MOM console. Other
management packages may have similar requirements. The filter action for the OnePoint client can be
configured to negotiate IPSec with the MOM server if an even greater level of security is desired. This
IPSec policy will effectively block traffic through random high ports, therefore disallowing remote
procedure call (RPC) traffic. This can make management of the server difficult. Because so many ports
have been effectively closed, Terminal Services has been enabled. This will allow administrators to
perform remote administration.
The network traffic map above assumes that the environment contains Active Directory enabled DNS
servers. If stand-alone DNS servers are used, additional rules may be required. The implementation
of IPSec policies should not have a noticeable impact on the performance of the server. However,
testing should be performed before implementing these filters to verify that the necessary functionality
and performance of the server is maintained. Additional rules may also need to be added to support
other applications.
Included with the Microsoft’s “Windows Server 2003 Security Guide: Patterns and Practices” security
guide is a .cmd file that simplifies the creation of the IPSec filters prescribed for a domain controller.
The PacketFilters-Print.cmd file uses the NETSH command to create the appropriate filters. This .cmd
file must be modified to include the IP addresses of the other domain controllers in the environment.
The script contains place holders for two domain controllers to be added. Additional domain
controllers can be added if desired. This list of IP addresses for the domain controllers must be kept up
to date. If MOM is present in the environment, the IP address of the appropriate MOM server must
also be specified in the script. This script does not create persistent filters. Therefore, the server will
be unprotected until the IPSec Policy Agent starts. For more information on building persistent filters or
creating more advanced IPSec filter scripts, see Chapter 11, "Additional Member Server Hardening
Procedures" in Microsoft’s “Windows Solution for Security: Threats and Countermeasures: Security
Settings in Windows Server 2003 and Windows XP”. Finally, this script is configured to not assign
the IPSec policy it creates. The IP Security Policy Management snap-in can be used to examine the
IPSec filters created, and to assign the IPSec policy in order for it to take effect.
2.10.7
HP NAS Specific Security Settings
The hardening of specific HP NAS accounts and applications are required to meet NSA security
compliancy.