91
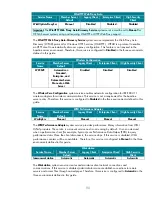
World Wide Web Publishing Service
Service Name
Member Server
Default
Legacy Client
Enterprise Client High Security Client
W3SVC Not
installed Disabled Disabled Disabled
Important:
The
World Wide Web Publishing Service
system service must be set to
Automatic
for HP
NAS server systems in which the HP NAS WEB GUI interface is used, HP Insight Manager is used,
HP’s Array Configuration Utility (ACU) is used, HTTP file shares are created, or FTP file shares are
created.
The
World Wide Web Publishing Service
system service provides Web connectivity and administration
through the Internet Information Service snap-in. This service is not a requirement for the baseline
server policy. Therefore, this service is configured to
Disabled
in the three environments defined in this
guide.
2.8.6
Additional Security Settings
Additional registry value entries were created for the baseline security template files that are not
defined within the Administrative Template (.adm) file for the three security environments defined in
this guide. The .adm file defines the system policies and restrictions for the desktop, shell, and security
for Windows Server 2003 and Windows Storage Server 2003 systems. These settings are
embedded within the security templates, in the Security Options section, to automate the changes. If
the policy is removed, these settings are not automatically removed with it and must be manually
changed by using a registry editing tool such as Regedt32.exe. The same registry values are applied
across all three environments.
This guide includes additional settings added to the Security Configuration Editor (SCE) by modifying
the sceregvl.inf file, located in the %windir%\inf folder, and re-registering scecli.dll. The original
security settings, as well as the additional ones, appear under Local Policies\Security in the snap-ins
and tools listed previously in this section. The customization to sceregvl.inf provided below uses
features only available on Microsoft Windows® XP Professional with Service Pack 1 and Windows
Server 2003. Administrators should not try to install it on older versions of Windows.
Once the Sceregvl.inf file has been modified and registered, the custom registry values are exposed
in the SCE user interfaces on that computer. Administrators will see the new settings at the bottom of
the list of items in the SCE which are all preceded by the text "MSS." MSS stands for Microsoft
Solutions for Security, the name of the group that created this guide. Administrators can then create
security templates or policies that define these new registry values. These templates or policies can
then be applied to any computer regardless of whether Sceregvl.inf has been modified on the target
computer or not. Subsequent launches of the SCE UI’s exposes any custom registry values.
Administrators must complete the following procedural steps to update the sceregvl.inf file:
1.
Open the %systemroot%\inf\sceregvl.inf file in a text editor such as Notepad.
2.
Navigate to the bottom of the
[Register Registry Values]
section and copy the following text into
the file:
;================================ MSS Values ================================
MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters\EnableICMPRedirect,4,%EnableICMPRedirect%,0
MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters\SynAttackProtect,4,%SynAttackProtect%,3,0|%SynAttackPr
otect0%,1|%SynAttackProtect1%
MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters\EnableDeadGWDetect, 4,%EnableDeadGWDetect%,0
MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters\EnablePMTUDiscovery,4,%EnablePMTUDiscovery%,0