125
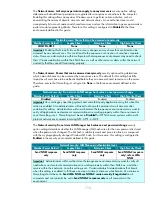
Windows System Resource Manager
Service Name
Member Server
Default
Legacy Client
Enterprise Client High Security Client
WindowsSystem
ResourceManager
Not installed
Disabled
Disabled
Disabled
Important:
The
Windows System Resource Manager (WSRM)
system service must be set to
Automatic
for HP NAS server systems that are used to deploy applications.
The
Windows System Resource Manager
(WSRM) system service is a tool to help customers deploy
applications into consolidation scenarios. This feature is not required in the baseline server
environment. Therefore, this service is configured to
Disabled
in the three environments defined in this
guide.
2.9.6
Additional Security Settings
The security settings applied through the MSBP provide a great deal of enhanced security for file
servers. Nevertheless, there are a few additional considerations that should be taken into account.
These steps cannot be completed via Group Policy and should be performed manually on all file
servers.
2.9.6.1
Disable Auto Generation of 8.3 File Names: Enable the computer to stop generating 8.3
style filenames
This entry appears as
MSS: Enable the computer to stop generating 8.3 style filenames
in the SCE.
Windows Server 2003 supports 8.3 file name formats for backward compatibility with16-bit
applications. The 8.3 file name convention is a naming format that allows file names that are up to
eight characters in length. The following registry value entry has been added to the template in the
registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\FileSystem\
Subkey Registry Value Entry
Format
Recommended Value (Decimal)
NtfsDisable8dot3NameCreation DWORD
1
Important:
Various 3
rd
party applications may not install nor function correctly if this registry setting is
set to
1.
It is recommended that the
NtfsDisable8dot3NameCreation
setting remains as
0.
2.9.6.2
Securing Well Known Accounts
Microsoft Windows Server. 2003 has a number of built-in user accounts that cannot be deleted but
can be renamed. Two of the most well known built-in accounts in Windows 2003 are
Guest
and
Administrator
. The
Guest
account is disabled by default on member servers and domain controllers.
This setting should not be changed. The built-in
Administrator
account should be renamed and the
description altered to help prevent attackers from compromising a remote server using a well known
account. Many variations of malicious code use the built-in administrator account in an initial attempt
to compromise a server. The value of this configuration change has diminished over the past few
years since the release of attack tools that attempt to break into the server by specifying the security
identifier (SID) of the built-in
Administrator
account to determine its true name. A SID is the value that
uniquely identifies each user, group, computer account, and logon session on a network. It is not
possible to change the SID of this built-in account. Renaming the local administrator account to a