C
HAPTER
3
| Using the Web Interface
Navigating the Web Browser Interface
– 98 –
N
OTE
:
Connection to the web interface is not supported for HTTPS using an
IPv6 link local address.
N
AVIGATING
THE
W
EB
B
ROWSER
I
NTERFACE
To access the web-browser interface you must first enter a user name and
password. The administrator has Read/Write access to all configuration
parameters and statistics. The default user name and password for the
administrator is “admin.” The administrator has full access privileges to
configure any parameters in the web interface. The default user name and
password for guest access is “guest.” The guest only has read access for
most configuration parameters. Refer to
"Configuring User Accounts" on
page 324
for more details.
H
OME
P
AGE
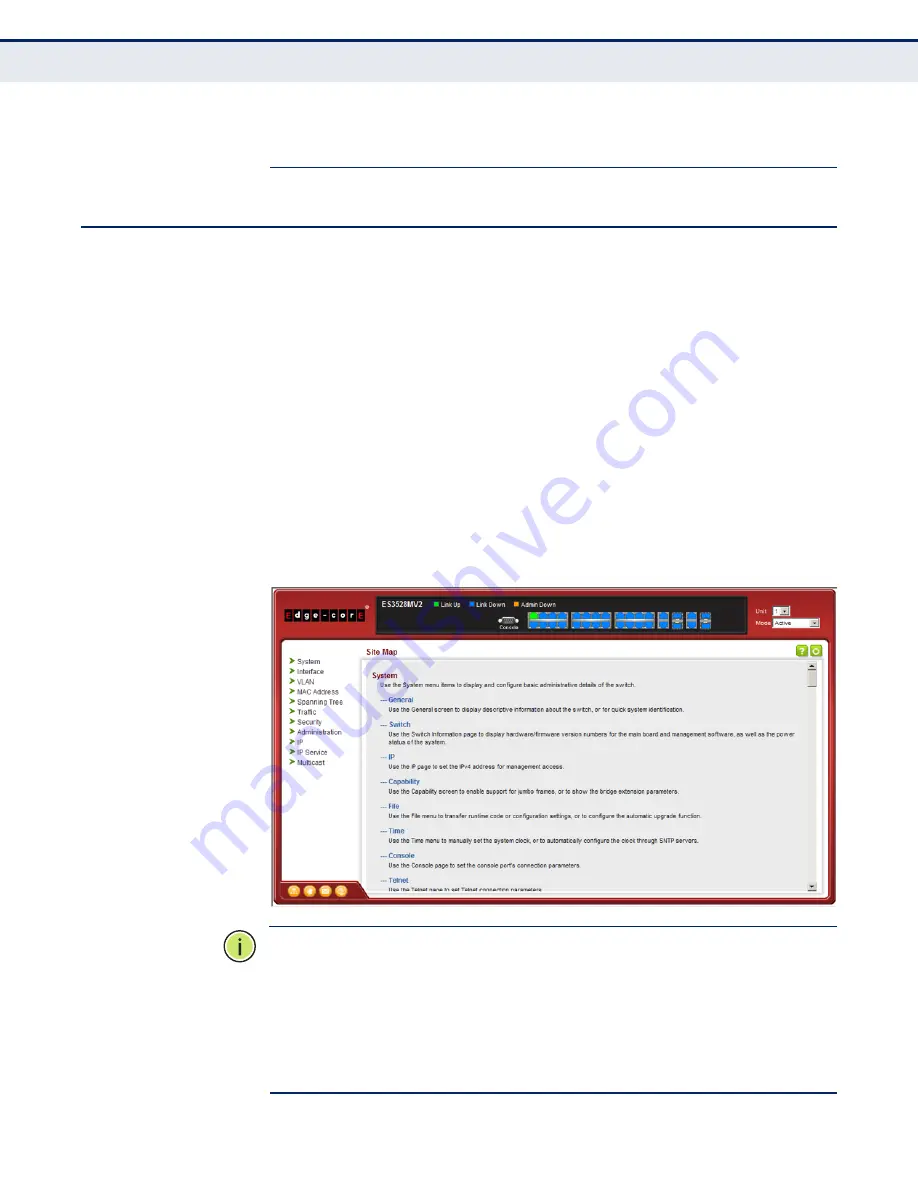
When your web browser connects with the switch’s web agent, the home
page is displayed as shown below. The home page displays the Main Menu
on the left side of the screen and System Information on the right side. The
Main Menu links are used to navigate to other menus, and display
configuration parameters and statistics.
Figure 1: Home Page
N
OTE
:
This manual covers the ES3528MV2 and ES3528MV2-DC Fast
Ethernet switches. There are no significant differences in the user interface
for these switches, so all of the screen display examples are based on the
ES3528MV2. The panel graphics for both switch types are shown on the
following page.
N
OTE
:
You can open a connection to the vendor’s web site by clicking on
the Edge-Core logo.
Summary of Contents for ES3528MV2
Page 1: ...Management Guide www edge core com ES3528MV2 ES3528MV2 DC 28 Port Fast Ethernet Layer 2 Switch...
Page 2: ......
Page 4: ......
Page 48: ...CONTENTS 48...
Page 68: ...SECTION I Getting Started 68...
Page 78: ...CHAPTER 1 Introduction System Defaults 78...
Page 96: ...SECTION II Web Configuration 96...
Page 116: ...CHAPTER 3 Using the Web Interface Navigating the Web Browser Interface 116...
Page 148: ...CHAPTER 4 Basic Management Tasks Resetting the System 148...
Page 192: ...CHAPTER 5 Interface Configuration VLAN Trunking 192 Figure 65 Configuring VLAN Trunking...
Page 226: ...CHAPTER 6 VLAN Configuration Configuring VLAN Translation 226...
Page 236: ...CHAPTER 7 Address Table Settings Configuring MAC Address Mirroring 236...
Page 270: ...CHAPTER 9 Congestion Control Automatic Traffic Control 270...
Page 300: ...CHAPTER 11 Quality of Service Attaching a Policy Map to a Port 300...
Page 418: ...CHAPTER 13 Security Measures DHCP Snooping 418...
Page 588: ...CHAPTER 15 IP Configuration Setting the Switch s IP Address IP Version 6 588...
Page 606: ...CHAPTER 16 IP Services Configuring the PPPoE Intermediate Agent 606...
Page 676: ...CHAPTER 17 Multicast Filtering Multicast VLAN Registration for IPv6 676...
Page 772: ...CHAPTER 20 System Management Commands Switch Clustering 772...
Page 802: ...CHAPTER 22 Remote Monitoring Commands 802...
Page 808: ...CHAPTER 23 Flow Sampling Commands 808...
Page 872: ...CHAPTER 24 Authentication Commands PPPoE Intermediate Agent 872...
Page 950: ...CHAPTER 25 General Security Measures Port based Traffic Segmentation 950...
Page 1002: ...CHAPTER 27 Interface Commands Power Savings 1002...
Page 1016: ...CHAPTER 28 Link Aggregation Commands Trunk Status Display Commands 1016...
Page 1046: ...CHAPTER 30 Congestion Control Commands Automatic Traffic Control Commands 1046...
Page 1058: ...CHAPTER 32 UniDirectional Link Detection Commands 1058...
Page 1064: ...CHAPTER 33 Address Table Commands 1064...
Page 1124: ...CHAPTER 35 ERPS Commands 1124...
Page 1168: ...CHAPTER 36 VLAN Commands Configuring Voice VLANs 1168...
Page 1182: ...CHAPTER 37 Class of Service Commands Priority Commands Layer 3 and 4 1182...
Page 1202: ...CHAPTER 38 Quality of Service Commands 1202...
Page 1360: ...CHAPTER 41 CFM Commands Delay Measure Operations 1360...
Page 1382: ...CHAPTER 43 Domain Name Service Commands 1382...
Page 1440: ...SECTION IV Appendices 1440...
Page 1468: ...COMMAND LIST 1468...
Page 1479: ......
Page 1480: ...ES3528MV2 ES3528MV2 DC E112013 ST R03...
















































