A
PPENDICES
S
ECTION
A
PPENDIX
C
8
E
6 T
ECHNOLOGIES
,
T
HREAT
A
NALYSIS
R
EPORTER
U
SER
G
UIDE
199
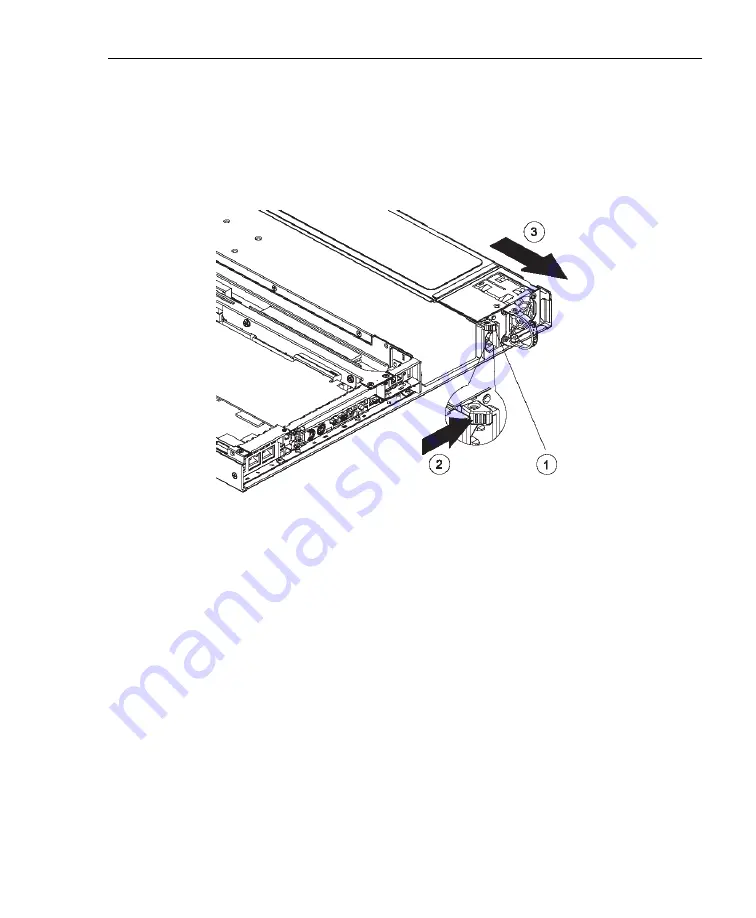
Step 3: Replace the failed power supply
Remove the failed power supply by locating the red release
tab (1) and pushing it to the right (2), then lifting the curved
metal handle and pulling the power supply module towards
you (3).
Note that an audible alarm sounds and the LED is unlit
when the power supply is disengaged. Replace the failed
power supply with your spare replacement power supply.
The alarm will turn off and the LED will be a steady green
when the replacement power supply is securely locked in
place.
Step 4: Contact Technical Support
Contact Technical Support to order a new replacement
power supply and for instructions on returning your failed
power supply to 8e6.
Summary of Contents for TAR
Page 1: ... Threat Analysis Reporter USER GUIDE Model TAR Release 1 3 00 Manual Version 1 01 ...
Page 2: ...ii 8E6 TECHNOLOGIES THREAT ANALYSIS REPORTER USER GUIDE ...
Page 4: ...iv 8E6 TECHNOLOGIES THREAT ANALYSIS REPORTER USER GUIDE ...
Page 216: ...APPENDICES SECTION APPENDIX D 204 8E6 TECHNOLOGIES THREAT ANALYSIS REPORTER USER GUIDE ...


























