410
C
HAPTER
B: RADIUS S
ERVER
AND
RADIUS C
LIENT
S
ETUP
p
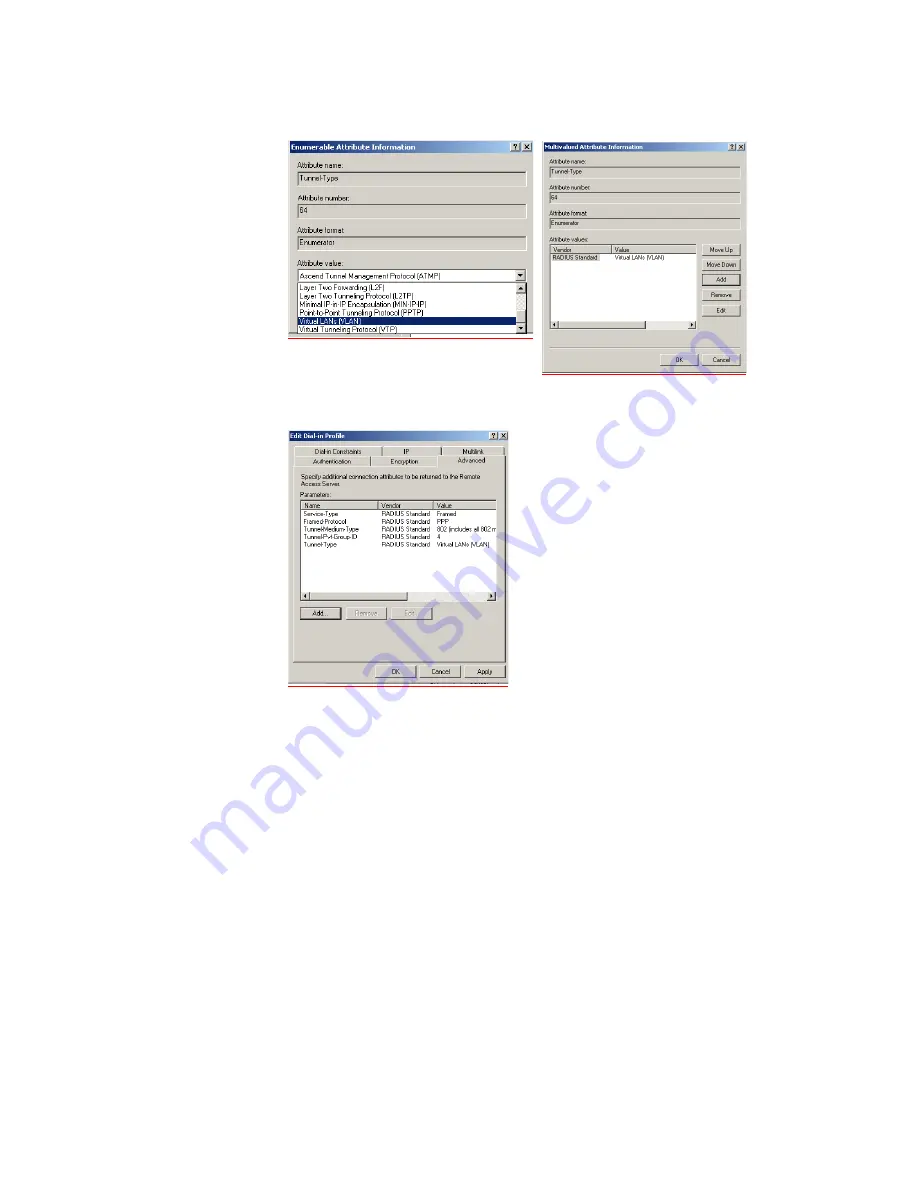
Click
Add
again. In the pull down menu, select
Virtual LANs
and click
OK
.
q
Click
OK
again and to return to the
Add Attributes
screen. Click
Close
. You will
now see the added attributes
r
Click
OK
to close the
Profile
screen and
OK
again to close the
Policy
screen.
This completes the configuration of the Internet Authentication Service.
2
To test the configuration, connect the workstation to a port on the Switch
5500G-EI (the port does not have to be a member of VLAN 4). Ensure that there is
a DHCP server connected to the switch that resides on a switch port that is an
untagged member of VLAN 4. The RADIUS server should reside in the same VLAN
as the workstation.
Once authenticated the switch will receive VLAN information from the RADIUS
server and will place the switch port in the associated VLAN.
For troubleshooting, you can use the Event Viewer on both the workstation and
the RADIUS server.
Configuring Funk
RADIUS
3Com has successfully installed and tested Funk RADIUS running on a Windows
server in a network with Switch 5500G-EI deployed.
Download the Funk Steel-Belted RADIUS Server application from
www.funk.com
and install the application. Once installed you have a 30 day license to use it.
Summary of Contents for SuperStack 4
Page 6: ...18 ABOUT THIS GUIDE ...
Page 34: ...46 CHAPTER 1 GETTING STARTED ...
Page 62: ...74 CHAPTER 3 VLAN OPERATION ...
Page 69: ...PoE Configuration 81 ...
Page 70: ...82 CHAPTER 4 POWER OVER ETHERNET POE CONFIGURATION ...
Page 98: ...110 CHAPTER 5 NETWORK PROTOCOL OPERATION ...
Page 220: ...232 CHAPTER 8 ACL CONFIGURATION ...
Page 408: ...420 CHAPTER B RADIUS SERVER AND RADIUS CLIENT SETUP ...
Page 432: ...444 APPENDIX D 3COM XRN ...






























