Chapter 6 The WIFI Configuration Screen
User’s Guide
62
Security
Security stops unauthorized devices from using the wireless network. It can also
protect the information that is sent in the wireless network.Use the strongest
security that every wireless client in the wireless network supports.
Note: WPA2 or WPA2-PSK security is recommended.
• WPA2-PSK and WPA-PSK do not employ user authentication and are known as
the personal version of WPA.
• WEP is better than no security, but it is still possible for unauthorized devices to
figure out the original information pretty quickly.
AES
Advanced Encryption Standard is method of data encryption that uses a secret
key. AES may use a 128-bit, 192-bit or 256-bit key. AES is faster than 3DES.
TKIP
Temporal Key Integrity Protocol (TKIP) is an encryption protocol that uses 128-bit
keys that are dynamically generated and distributed by the authentication server.
TKIP regularly changes and rotates the encryption keys so that the same
encryption key is never used twice.
MAC Address Filter
Every Ethernet device has a unique MAC (Media Access Control) address. The MAC
address consists of twelve hexadecimal characters (0-9, and A to F), and it is
usually written in the following format: “0A:A0:00:BB:CC:DD”.
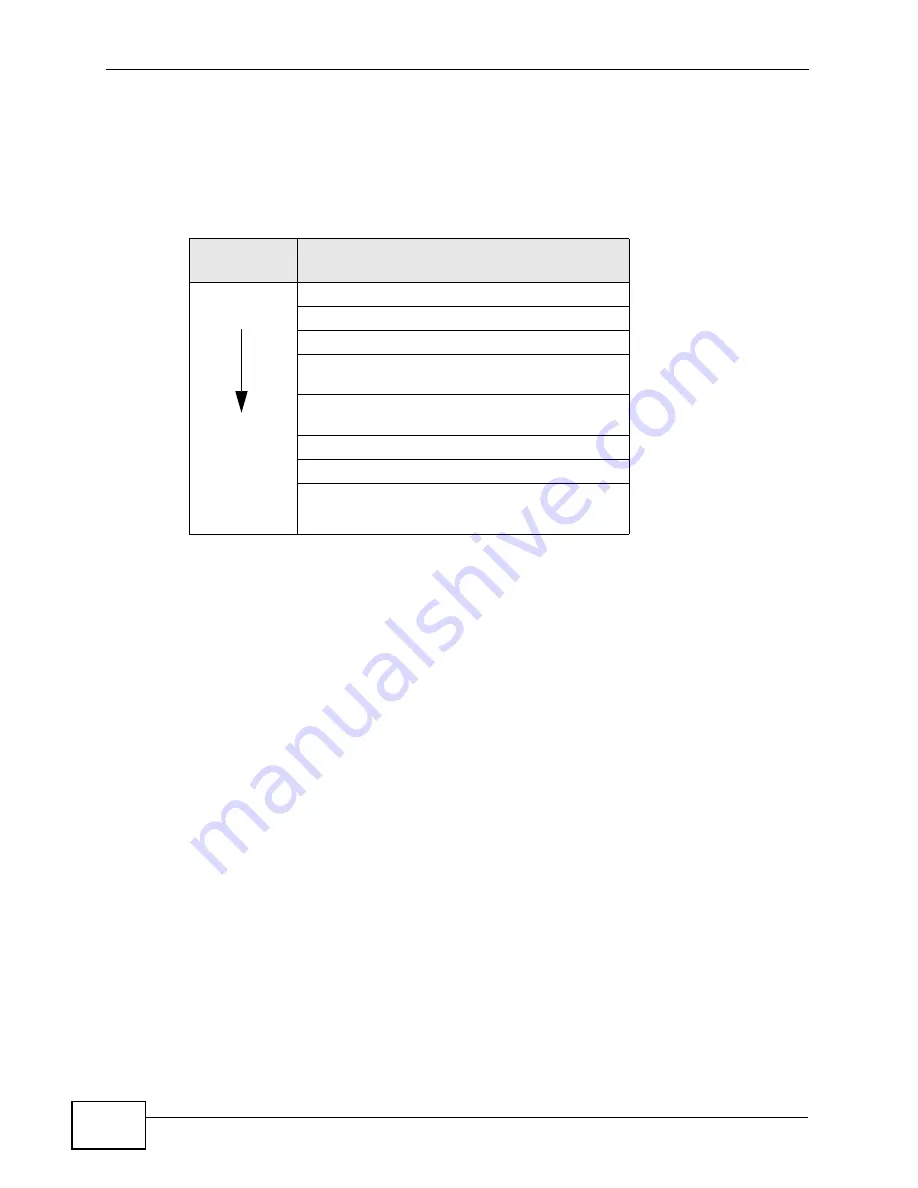
Table 17
Wireless Security Levels
SECURITY
LEVEL
SECURITY TYPE
Weakest
Strongest
No Security
MAC Address Filtering
WEP Encryption
IEEE 802.1x EAP with RADIUS Server
Authentication
WPA-PSK (Wi-Fi Protected Access Pre-Shared
Key)
WPA (Wi-Fi Protected Access)
WPA-PSK2
WPA2
Содержание MAX-207HW2
Страница 7: ...Safety Warnings User s Guide 8...
Страница 9: ...Contents Overview User s Guide 10...
Страница 16: ...17 PART I Introduction and Wizards Getting Started 19 Introducing the Web Configurator 23...
Страница 17: ...18...
Страница 27: ...Chapter 2 Introducing the Web Configurator User s Guide 28...
Страница 28: ...29 PART II Basic Screens The Main Screen 25 The Setup Screens 31...
Страница 29: ...30...
Страница 37: ...Chapter 3 The Setup Screens User s Guide 38...
Страница 39: ...40...
Страница 43: ...Chapter 4 The Status Screen User s Guide 44...
Страница 57: ...Chapter 5 The LAN Configuration Screens User s Guide 58...
Страница 75: ...Chapter 6 The WIFI Configuration Screen User s Guide 76...
Страница 87: ...Chapter 7 The WAN Configuration Screens User s Guide 88...
Страница 97: ...Chapter 8 The NAT Configuration Screens User s Guide 98...
Страница 106: ...107 PART IV Voice Screens The Service Configuration Screens 109 The Phone Screens 127 The Phone Book Screens 137...
Страница 107: ...108...
Страница 125: ...Chapter 10 The Service Configuration Screens User s Guide 126...
Страница 141: ...Chapter 12 The Phone Book Screens User s Guide 142...
Страница 143: ...144...
Страница 147: ...Chapter 13 The Certificates Screens User s Guide 148...
Страница 159: ...Chapter 14 The Remote Management Screens User s Guide 160...
Страница 165: ...Chapter 16 The Status Screen User s Guide 166...
Страница 166: ...167 PART VI Troubleshooting and Specifications Troubleshooting 169 Product Specifications 177...
Страница 167: ...168...
Страница 175: ...Chapter 17 Troubleshooting User s Guide 176...






























