DefensePro User Guide
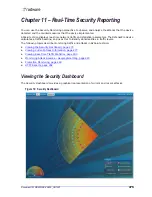
Real-Time Security Reporting
Document ID: RDWR-DP-V0602_UG1201
287
Attack Info
The attack information comprises the following parameters:
•
Protection State—The state of the protection process:
—
Characterization—The protection module is analyzing the
attack footprint.
—
Mitigation—The protection module is mitigating the attack
according to the profile configuration.
—
Suspicious Activities—The protection module identified
the attack but cannot mitigate it.
•
Mitigation Flow—The configuration of the mitigation flow for
the profile:
—
Default—The mitigation flow for the profile is configured
to use all three mitigation actions, which are selected by
default: 1-Challenge Suspects, 2-Challenge All, 3-Block
Suspects.
—
Customized—The mitigation flow for the profile is not
configured to use all three mitigation actions.
•
Action—The current action that protection module is using to
mitigate the attack:
—
Challenge Suspected Attackers—The protection module is
challenging HTTP sources that match the real-time
signature.
—
Challenge All Sources—The protection module is
challenging all HTTP traffic toward the protected server.
—
Block Suspected Attackers—The protection module is
blocking all HTTP traffic from the suspect sources (that is,
sources that match the signature).
—
No Mitigation—The protection module is in the Suspicious
Activities state and is not mitigating the attack.
•
Challenge Method—The user-specified Challenge Method,
302 Redirect or JavaScript.
•
Suspicious Sources—The number of sources that the
protection module suspects as being malicious.
•
Challenged Sources—The number of sources that the
protection module has identified as being attackers and is
now challenging them.
•
Blocked Sources—The number of sources that the protection
module has identified as being attackers and is now blocking
them.
•
HTTP Authentication Table Utilization [%]—The percentage of
HTTP Authentication Table that is full.
Sampled Data
Opens the Sampled Data dialog box, which contains a data on
sampled attack packets.
Parameter
Description
Содержание DefensePro 6.02
Страница 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Страница 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Страница 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Страница 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Страница 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Страница 256: ...DefensePro User Guide Managing Device Operations and Maintenance 256 Document ID RDWR DP V0602_UG1201 ...
Страница 274: ...DefensePro User Guide Monitoring DefensePro Devices and Interfaces 274 Document ID RDWR DP V0602_UG1201 ...
Страница 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Страница 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Страница 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...