ProSecure Unified Threat Management (UTM) Appliance Reference Manual
9-12
Managing Users, Authentication, and Certificates
v1.0, January 2010
4.
Click
Apply
to save your settings. The user is added to the List of Users table.
To delete one or more users:
1.
In the List of Users table, select the checkbox to the left of the user that you want to delete or
click the
Select All
table button to select all users. You cannot delete a default user.
2.
Click the
Delete
table button.
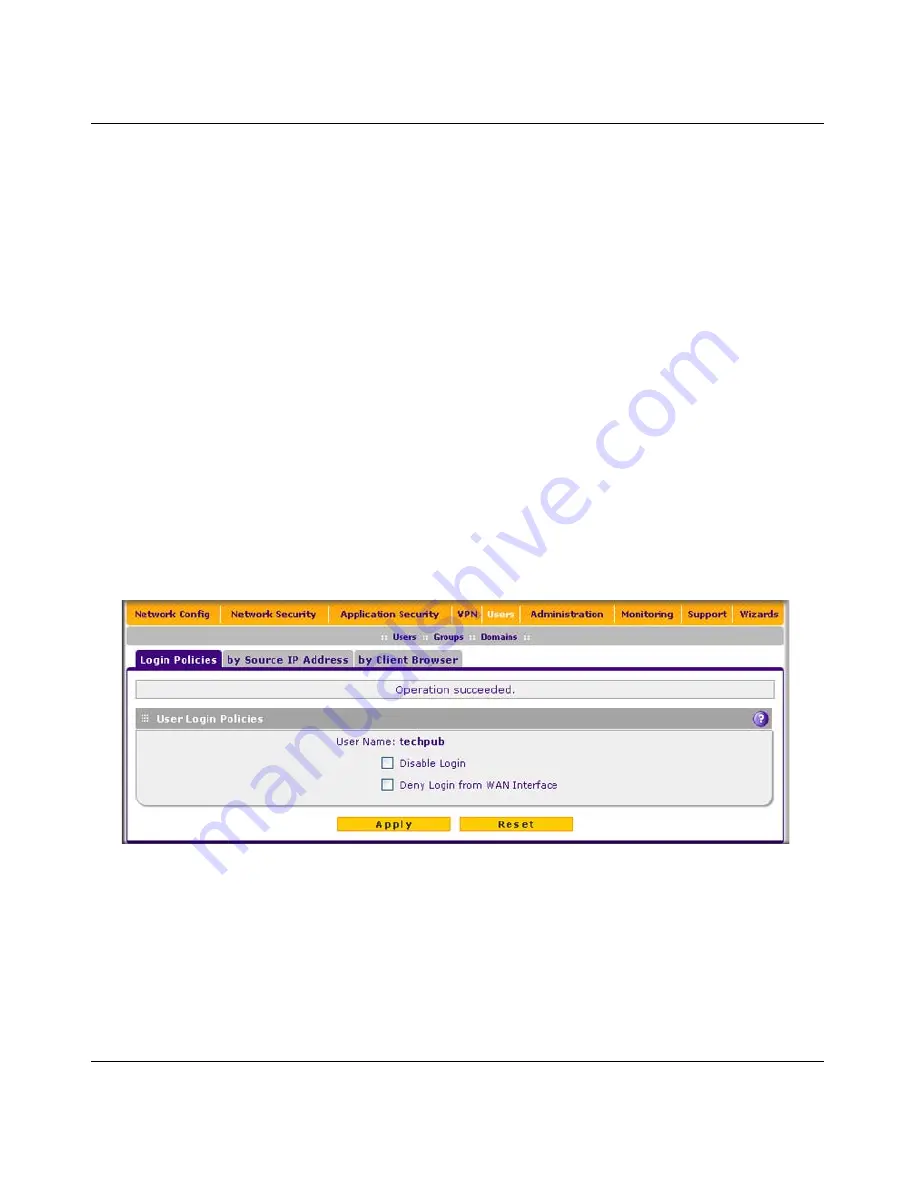
Setting User Login Policies
You can restrict the ability of defined users to log into the UTM’s Web management interface. You
can also require or prohibit logging in from certain IP addresses or from particular browsers.
Configuring Login Policies
To configure user login policies:
1.
Select
Users
>
Users
from the menu. The Users screen displays (see
Figure 9-5 on page 9-10
).
2.
In the Action column of the List of Users table, click the
Policies
table button for the user for
which you want to set login policies. The Policies submenu tabs appear, with the Login
Policies screen in view.
3.
In the User Login Policies section of the screen, make the following selections:
•
To prohibit this user from logging in to the UTM, select the
Disable Login
checkbox.
•
To prohibit this user from logging in from the WAN interface, select the
Deny Login from
WAN Interface
checkbox. In this case, the user can log in only from the LAN interface.
Figure 9-7
Содержание ProSecure
Страница 6: ...v1 0 January 2010 vi ...
Страница 16: ...ProSecure Unified Threat Management UTM Appliance Reference Manual xvi v1 0 January 2010 ...
Страница 34: ...ProSecure Unified Threat Management UTM Appliance Reference Manual 1 16 Introduction v1 0 January 2010 ...
Страница 114: ...ProSecure Unified Threat Management UTM Appliance Reference Manual 4 28 LAN Configuration v1 0 January 2010 ...
Страница 468: ...ProSecure Unified Threat Management UTM Appliance Reference Manual E 2 Related Documents v1 0 January 2010 ...






























