WF G
LOBAL
A
DMINISTRATOR
S
ECTION
C
HAPTER
1: S
YSTEM
SCREEN
M86 S
ECURITY
U
SER
G
UIDE
115
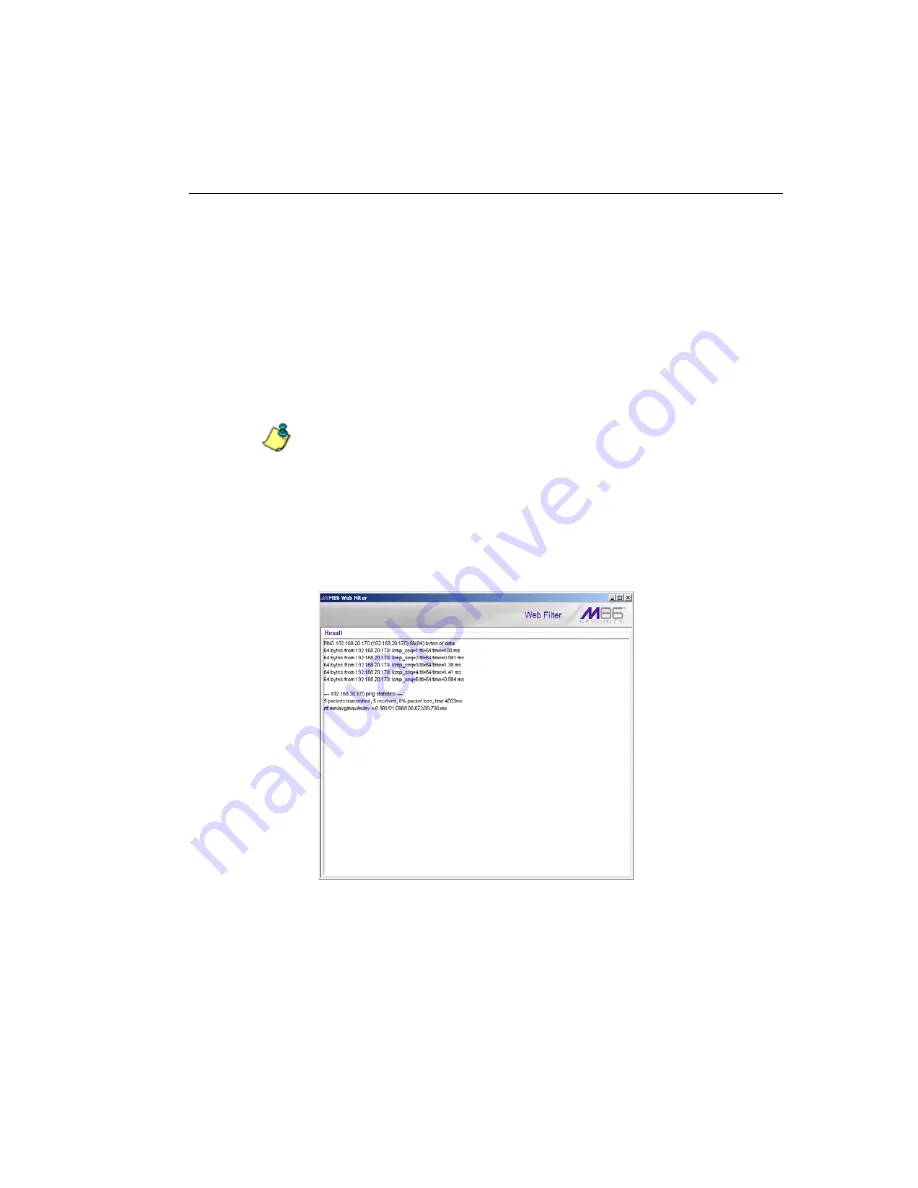
Perform a Diagnostic Test, View Data
1. Select a diagnostic tool from the
Command
pull-down
menu: ping(Ping), traceroute(Trace Route), ps(Process
list), top(TOP CPU processes), ifconfig(NIC configura-
tion), netstat(active connections), netstat(routing table),
free(current memory usage), iostat(CPU usage),
sar(system performance), recent logins, uptime(system
uptime), df(disk usage), and dmesg(print kernel ring
buffer).
NOTE
: See Command Selections for a list of commands and
their functions.
If “Ping” or “Trace Route” was selected from the pull-
down menu, a blank field displays to the right and must
be populated.
2. Click
Execute
to open a pop-up window containing the
query results:
Fig. 2:1-20 System Command, Results window
3. Click the “X” in the upper right corner of the pop-up
window to close it.
Содержание M86 Threat Analysis Reporter
Страница 1: ...M86 Web Filtering and Reporting Suite USER GUIDE Software Version 4 2 00 Document Version 10 10 11...
Страница 28: ...CONTENTS xxviii M86 SECURITY USER GUIDE INDEX 887...
Страница 518: ...WEB FILTER APPENDICES SECTION APPENDIX D 490 M86 SECURITY USER GUIDE Fig D 20 Mobile Client Package Contents page...
Страница 938: ...INDEX 910 M86 SECURITY USER GUIDE...






























