61
Manual
www.kraun.it
Configure Wireless Network Security
The following
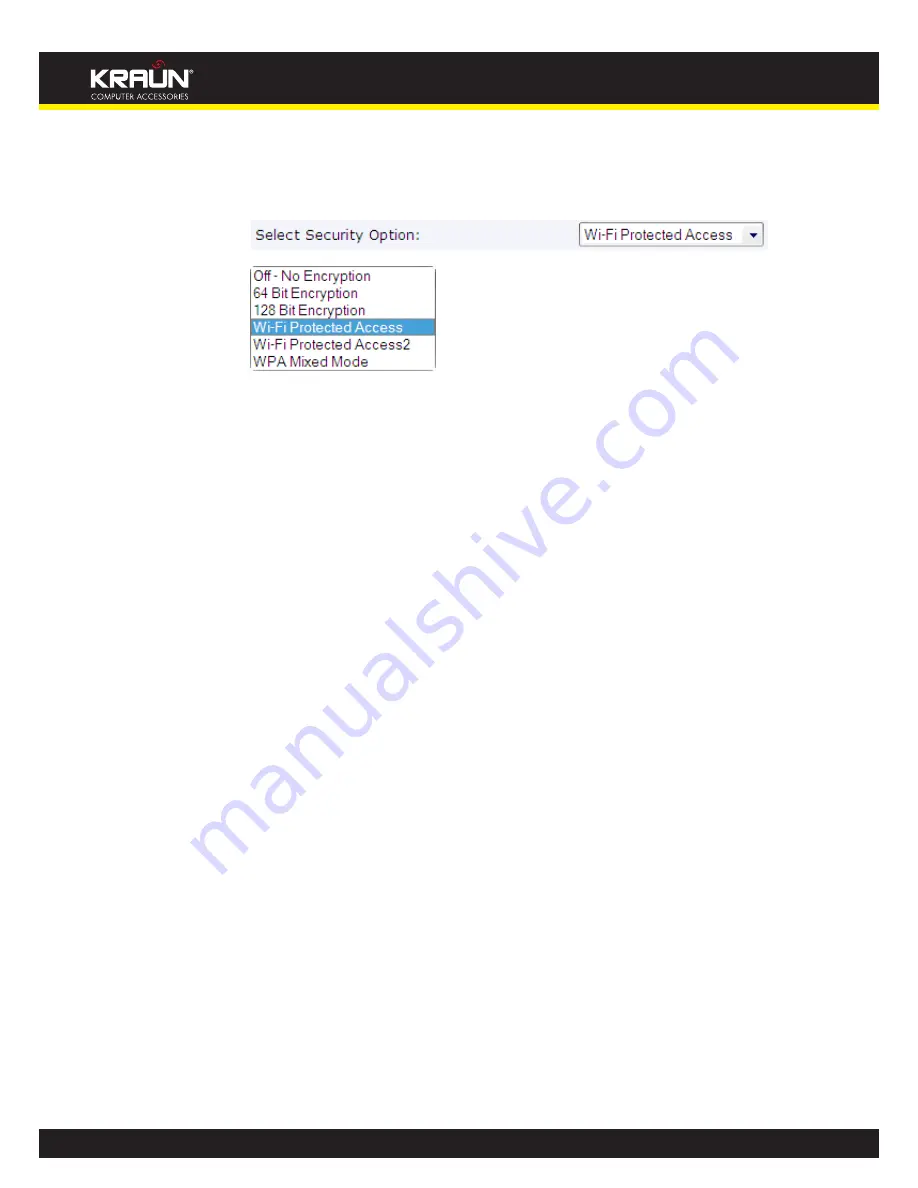
page allows you to configure wireless security:
Wireless Network: Security page
Figure 13:
You can protect your wireless data from potential
eavesdroppers
by encrypting wireless data
transmissions. An eavesdropper might set up a compatible wireless adapter within range of your
device and attempt to access your network. Data encryption is the translation of data into a form
that cannot be easily understood by unauthorized users.
There are two methods of wireless security to choose from:
Wired Equivalent Privacy (WEP)
•
; data is encrypted into blocks of either 64 bits length or
128 bits length. The encrypted data can only be sent and received by users with access
to a private network key. Each PC on your wireless network must be manually configured
with the same key as your device in order to allow wireless encrypted data transmissions.
Eavesdroppers cannot access your network if they do not know your private key. WEP is
considered to be a low security option.
Wi-Fi Protected Access (WPA)
•
; provides a stronger data encryption method (called Temporal
Key Integrity Protocol (TKIP)). It runs in a special, easy-to-set-up home mode called Pre-
Shared Key (PSK) that allows you to manually enter a pass phrase on all the devices in your
wireless network. WPA data encryption is based on a WPA master key. The master key is
derived from the pass phrase and the network name (SSID) of the device.
To configure security, choose one of the following options:
If you do not want to use Wireless Network security, click the
•
Off
radio button and then click
Next>.
Off
is the default setting, but you are
strongly recommended
to use wireless network
security on your device.
If you want to use WEP 64bit data encryption, follow the instructions in
•
Configuring 64bit bit
encryption
.
If you want to use WEP 128bit data encryption, follow the instructions in
•
Configuring 128bit bit
encryption
.
If you want to use WPA1 -
•
Wi-Fi Protected Access 1
, follow the instructions in
Configuring
WPA1 security
.
If you want to use WPA2 -
•
Wi-Fi Protected Access 2
, follow the instructions in
Configuring
WPA2 security
.
Содержание KR.XY
Страница 33: ...33 Manual www kraun it Click 24 Apply Click 25 Reboot The following page is displayed 26 ...
Страница 40: ...40 Manual www kraun it Click 20 Reboot The following page is displayed 21 ...
Страница 48: ...48 Manual www kraun it Click 23 Apply Click 24 Reboot The following page is displayed 25 ...
Страница 55: ...55 Manual www kraun it Click 26 Apply Click 27 Reboot The following page is displayed 28 ...
Страница 73: ...73 Manual www kraun it Click 6 Confirm ...
Страница 95: ...95 Manual www kraun it Enter VCI and VPI setting determined by your ISP 3 Click 4 Next ...
Страница 111: ...111 Manual www kraun it Now you are ready to Surf the Internet 15 ...
Страница 116: ...116 Manual www kraun it Click 15 Apply Your configuration is complete Now you are ready to Surf the Internet 16 ...
Страница 141: ...141 Manual www kraun it Click on 4 Go To Advanced view ...
Страница 147: ...147 Manual www kraun it Click 9 Dialing Plan tab Click 10 Go To Advanced view ...
Страница 148: ...148 Manual www kraun it Click 11 Add ...
Страница 155: ...155 Manual www kraun it Click 4 Add ...
Страница 159: ...159 Manual www kraun it Click 4 Add ...
Страница 163: ...163 Manual www kraun it Click 4 Add ...
Страница 167: ...167 Manual www kraun it Click 4 Add ...
Страница 171: ...171 Manual www kraun it Click 4 Add ...
Страница 175: ...175 Manual www kraun it Click 4 Edit on Policy Name ext int ...
Страница 176: ...176 Manual www kraun it Click 5 Enable of Status Click 6 Apply ...
Страница 180: ...180 Manual www kraun it Click 8 Continue Reboot Later ...
Страница 199: ...199 Manual www kraun it From the left hand 2 Services menu click on Dynamic DNS The following page is displayed ...
Страница 228: ...228 Manual www kraun it Click 5 restart Click 6 Restart ...






























