Shadow Copies
107
NAS 4000s and 9000s Administration Guide
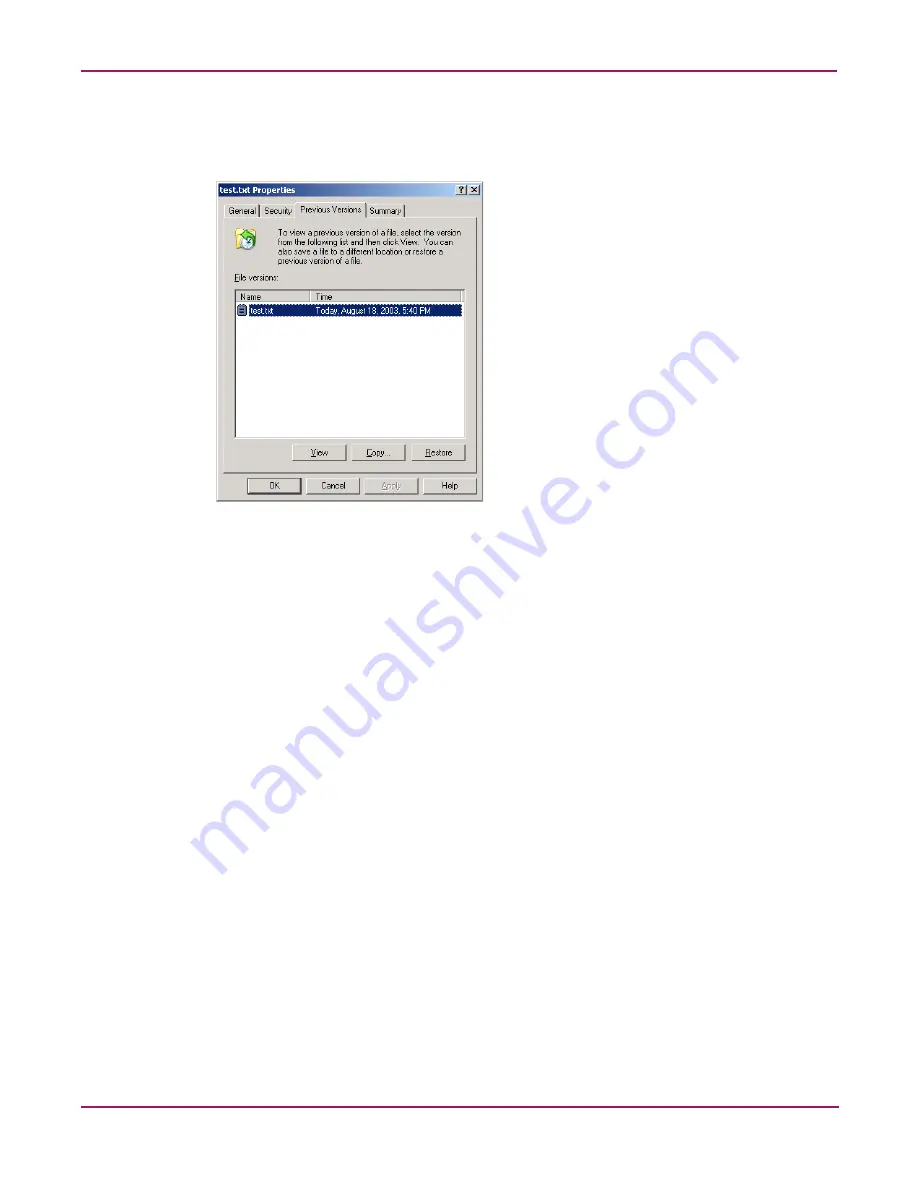
Users access shadow copies with Windows Explorer by selecting View, Copy, or Restore,
from the Previous Versions tab. See
Figure 55
. Both individual files and folders may be
restored.
Figure 55: Client GUI
When users view a network folder hosted on the NAS device for which shadow copies are
enabled, old versions (prior to the snapshot) of a file or directory are available. Viewing the
properties of the file or folder presents users with the folder or file history-a list of read-only,
point-in-time copies of the file or folder contents that users can then open and explore like any
other file or folder. Users can view files in the folder history, copy files from the folder history,
and so on.
NFS Shadow Copies
UNIX users can independently access previous versions of files stored on NFS shares via the
NFS client; no additional software is required. Server for NFS exposes each of a share's
available shadow copies as a pseudo-subdirectory of the share. Each of these
pseudo-subdirectories is displayed in exactly the same way as a regular subdirectory is
displayed.
The name of each pseudo-subdirectory reflects the creation time of the shadow copy, using the
[email protected]:MM:SS. Note that, to prevent common tools from
needlessly enumerating the pseudo-subdirectories, the name of each pseudo-subdirectory
begins with the dot character, thus rendering it hidden.
The following example shows an NFS share named “NFSShare” with three shadow copies,
taken on April 27, 28, and 29 of 2003 at 4 a.m.
NFSShare
[email protected]:00:00
[email protected]:00:00
[email protected]:00:00
Содержание NAS 4000s
Страница 18: ...About this Guide 18 NAS 4000s and 9000s Administration Guide ...
Страница 50: ...Basic Administrative Procedures and Setup Completion 50 NAS 4000s and 9000s Administration Guide ...
Страница 92: ...Disk Management 92 NAS 4000s and 9000s Administration Guide ...
Страница 196: ...NetWare File System Management 196 NAS 4000s and 9000s Administration Guide ...
Страница 246: ...Index 246 NAS 4000s and 9000s Administration Guide ...






























