xStack
®
DGS-3620 Series Layer 3 Managed Stackable Gigabit Switch Web UI Reference Guide
45
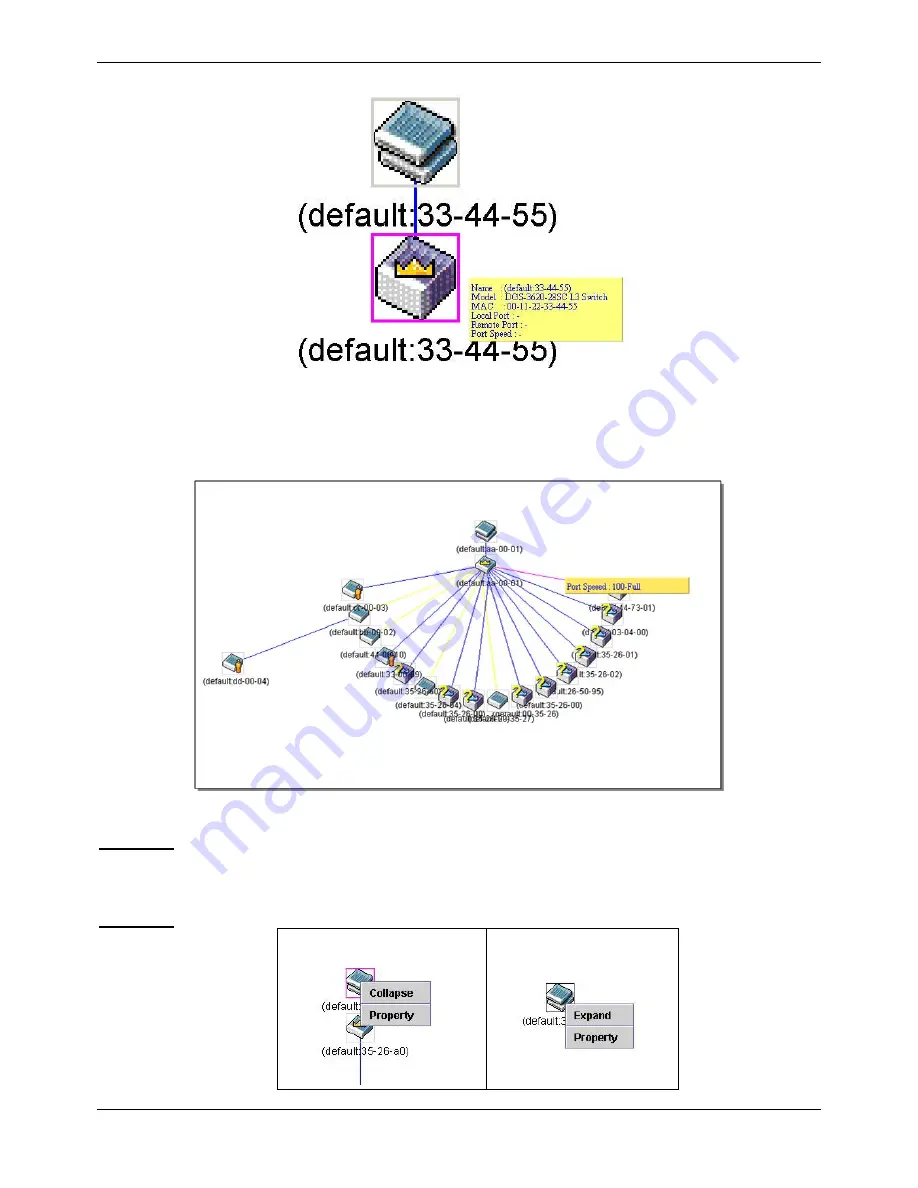
Figure 3-22 Device Information Utilizing the Tool Tip
Setting the mouse cursor over a line between two devices will display the connection speed between the two
devices, as shown below.
Figure 3-23 Port Speed Utilizing the Tool Tip
Right-clicking on a device will allow the user to perform various functions, depending on the role of the Switch in
the SIM group and the icon associated with it.
Right-Click
Group Icon
Содержание xStack DGS-3620-52P
Страница 1: ......






























