xStack® DGS-3120 Series Layer 3 Managed Gigabit Ethernet Switch Web UI Reference Guide
203
Parameter
Description
Originate
Select the status of the originating default information here. Selecting
Always
specifies
that the external default route will be originated, whether a default route exists or not.
Select
Default
specifies that the external default route will be originated only when one
default route already exists. Selecting
None
specifies that the external default route will
never be originated. This is the default option.
Metric Type
Select the type of LSA that contains the default external route imported into OSPF.
Metric (1-65535)
Enter the metric value used by the originating default external route here. This value
must be between 1 and 65535.
Click the
Apply
button to accept the changes made.
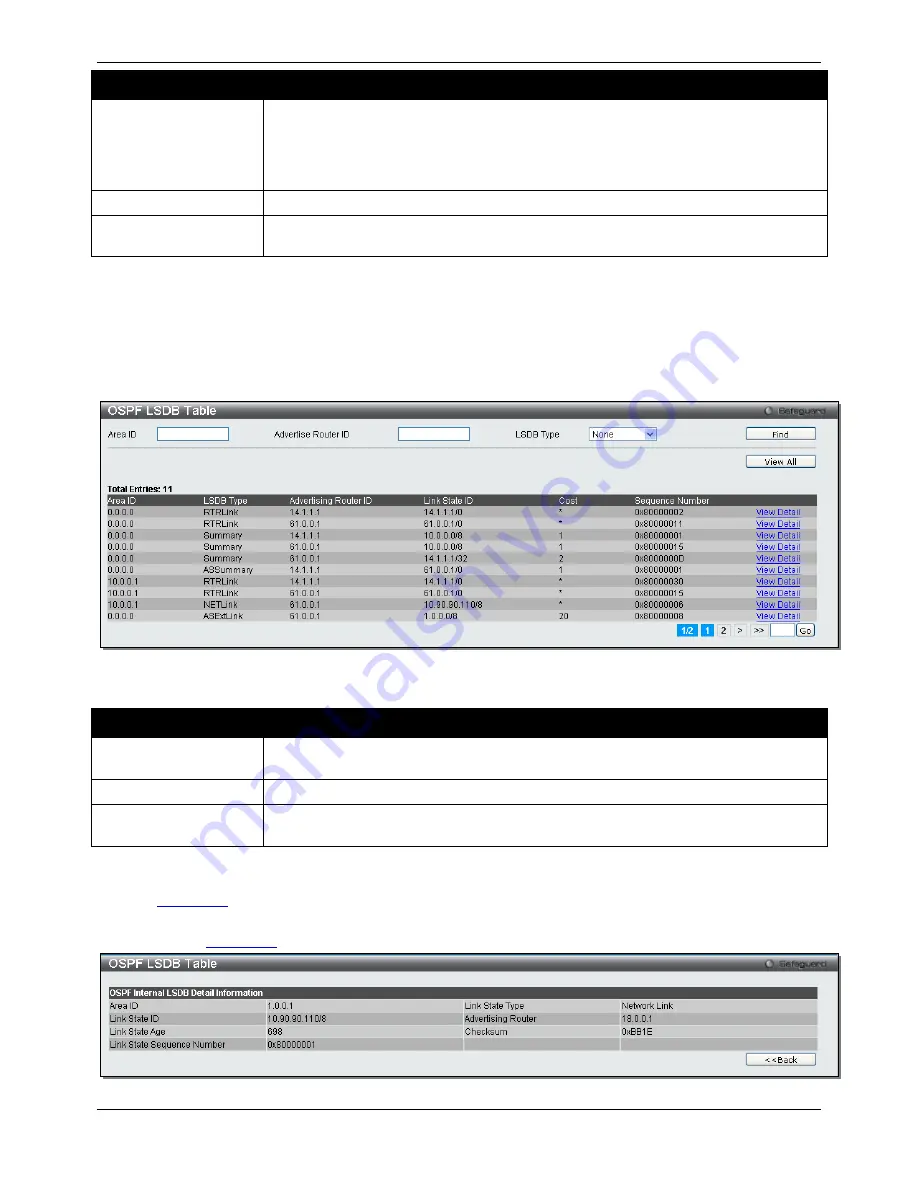
OSPF LSDB Table
This window is used to display the OSPF Link State Database (LSDB).
To view the following window, click
L3 Features > OSPF > OSPFv2 > OSPF LSDB Table
, as shown below:
Figure 5-54 OSPF LSDB Table window
The fields that can be configured are described below:
Parameter
Description
Area ID
Enter a 32-bit number in the form of an IP address (xxx.xxx.xxx.xxx) that uniquely
identifies the OSPF area in the OSPF domain.
Advertise Router ID
Enter the router ID of the advertising router.
LSDB Type
Specifies the LSDB type to be displayed. Options to choose from are
None
,
RTRLink
,
NETLink
,
Summary
,
ASSummary
,
ASExtLink
,
NSSA Ext
and
Stub
.
Click the
Find
button to find the specified entry.
Click the
View All
button to view all the OSPF Link State Database entries.
Click the
View Detail
link to view the OSPF LSDB details of the specific entry.
After clicking the
View Detail
link, the following window will appear:
Figure 5-55 OSPF LSDB Table – View Detail window
Содержание xStack DGS-3120 Series
Страница 1: ......






























