xStack® DGS-3120 Series Layer 3 Managed Gigabit Ethernet Switch Web UI Reference Guide
162
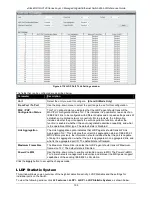
Figure 4-127 LLDP-MED Remote Port Information – Show Normal window
Click the
<<Back
button to return to the previous page.
NLB FDB Settings
The Switch supports Network Load Balancing (NLB). This is a MAC forwarding control for supporting the Microsoft
server load balancing application where multiple servers can share the same IP address and MAC address. The
requests from clients will be forwarded to all servers, but will only be processed by one of them. In multicast mode,
the client uses a multicast MAC address as the destination MAC to reach the server. Regardless of the mode, the
destination MAC is the shared MAC. The server uses its own MAC address (rather than the shared MAC) as the
source MAC address of the reply packet. The NLB multicast FDB entry will be mutually exclusive with the L2
multicast entry.
To view the following window, click
L2 Features > NLB FDB Settings
, as shown below:
Figure 4-128 NLB FDB Settings window
The fields that can be configured are described below:
Parameter
Description
Unicast
Click to create NLB unicast FDB entry.
Multicast
Click to NLB multicast FDB entry.
VLAN Name
Click the radio button and enter the VLAN of the NLB multicast FDB entry to be
created.
VID (1-4094)
Click the radio button and enter the VLAN by the VLAN ID.
MAC Address
Enter the MAC address of the NLB multicast/unicast FDB entry to be created.
Unit
Select the unit you wish to configure.
(EI and SI Mode Only)
Ports
Click the ports to be configured. Click the
All
button to select all ports.
Click the
Apply
button to accept the changes made.
Click the
Clear All
button to remove all the entered information in the fields.
Click the
Edit
button to update the information of the corresponding entry.
Click the
Delete
button to delete the corresponding entry.
Содержание xStack DGS-3120 Series
Страница 1: ......