Copyright (c) Fire4 Systems Inc, 2019. All rights reserved
5
Hackers pose two major threats to computer networks
The first threat to a computer network is to be hacked directly from the Internet. This is common
for a network that does not have a firewall, where all network devices are connected directly to a
router. Low cost routers have known exploits that permit the hacker to access the network
devices once the router type has been identified.
The second and more common threat is from the installation of a 'trojan' virus on one of the user
computers. The advantage of the trojan is that once installed, the trojan calls the hacker and
gives control of the computer to the hacker. This method can bypass completely a firewall with
inbound blocking. The trojan is usually installed via an email link or attachment that installs the
trojan software on the users computer. Most computer users are aware that they should not click
on email links or open attachments. However a hacker can bombard the employees of a company
with emails that duplicate the type of email that would be sent by a bank or a company such as
Facebook or Ebay to trick the user. Once the hacker has control of a users computer then that
computer can be used to hack into the data servers. The computer user has no idea that a
hacker is also sharing the computer, but may notice that the computer is running more slowly
than usual. Most successful hacks use the trojan virus method.
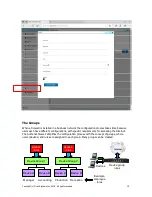
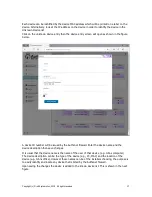
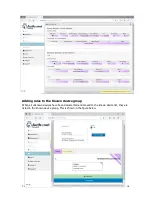
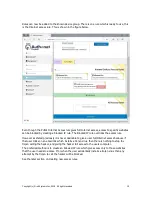
Using The Authonet Firewall
The Authonet firewall departs from conventional firewall design and permits a secure firewall to
be installed by people who have limited technical knowledge. The Authonet firewall was designed
to be installed by a person who knows how to use a computer and who can install a DSL router.
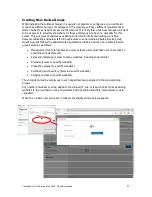
The Authonet Firewall is installed in the network between the DSL router and all other network
components. This is easily done and entails swapping two Ethernet cables. The connection of the
firewall is shown in the figure below.
1
1/7/17
Internet
Internet
DSL/ Cable
router
LAN
port
Laptop
WAN
port
Switch or
VLAN switch
Wireless access points
Multi-OS servers and services
USER SUBNET
Smart phone
Tablet
Desktops
AUTHONET
Admin
Authonet Firewall