Chapter 6 Wireless LAN
P-660W-Tx v2 User’s Guide
79
Unauthorized devices can still see the information that is sent in the wireless network, even if
they cannot use the wireless network. Furthermore, there are ways for unauthorized wireless
users to get a valid user name and password. Then, they can use that user name and password
to use the wireless network.
Local user databases also have an additional limitation that is explained in the next section.
Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
The types of encryption you can choose depend on the type of user authentication. (See
for information about this.)
For example, if the wireless network has a RADIUS server, you can choose
WPA
or
WPA2
. If
users do not have to log in with a user name and password in order to access the wireless
network, you can choose no encryption,
Static WEP
,
WPA-PSK
, or
WPA2-PSK
.
Usually, you should set up the strongest encryption that every wireless client in the wireless
network supports. For example, suppose the AP does not have a local user database, and you
do not have a RADIUS server. Therefore, there is no user authentication. Suppose the wireless
network has two wireless clients. Device A only supports WEP, and device B supports WEP
and WPA. Therefore, you should set up
Static WEP
in the wireless network.
"
It is recommended that wireless networks use
WPA-PSK
,
WPA
, or stronger
encryption. IEEE 802.1x and WEP encryption are better than none at all, but it
is still possible for unauthorized devices to figure out the original information
pretty quickly.
"
It is not possible to use
WPA-PSK
,
WPA
or stronger encryption with a local
user database. In this case, it is better to set up stronger encryption with no
authentication than to set up weaker encryption with the local user database.
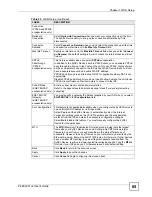
Table 23
Types of Encryption for Each Type of Authentication
NO AUTHENTICATION
RADIUS SERVER
Weakest
No Security
WPA
Static WEP
WPA-PSK
Strongest
WPA2-PSK
WPA2
Summary of Contents for P-660W-T1 v2
Page 2: ......
Page 8: ...Safety Warnings P 660W Tx v2 User s Guide 8 ...
Page 10: ...Contents Overview P 660W Tx v2 User s Guide 10 ...
Page 18: ...Table of Contents P 660W Tx v2 User s Guide 18 ...
Page 22: ...List of Figures P 660W Tx v2 User s Guide 22 ...
Page 25: ...25 PART I Introduction Introducing the ZyXEL Device 27 Introducing the Web Configurator 31 ...
Page 26: ...26 ...
Page 30: ...Chapter 1 Introducing the ZyXEL Device P 660W Tx v2 User s Guide 30 ...
Page 36: ...Chapter 2 Introducing the Web Configurator P 660W Tx v2 User s Guide 36 ...
Page 37: ...37 PART II Setup Wizard Connection Setup Wizard 39 Media Bandwidth Management Wizard 47 ...
Page 38: ...38 ...
Page 46: ...Chapter 3 Connection Setup Wizard P 660W Tx v2 User s Guide 46 ...
Page 50: ...Chapter 4 Media Bandwidth Management Wizard P 660W Tx v2 User s Guide 50 ...
Page 52: ...52 ...
Page 83: ...Chapter 7 WAN Setup P 660W Tx v2 User s Guide 83 Figure 32 WAN Setup PPPoE ...
Page 104: ...Chapter 8 Network Address Translation NAT Screens P 660W Tx v2 User s Guide 104 ...
Page 130: ...Chapter 11 Firewall Configuration P 660W Tx v2 User s Guide 130 ...
Page 156: ...Chapter 15 Logs Screens P 660W Tx v2 User s Guide 156 ...
Page 169: ...169 PART IV Maintenance Maintenance 171 ...
Page 170: ...170 ...
Page 184: ...Chapter 17 Maintenance P 660W Tx v2 User s Guide 184 ...
Page 185: ...185 PART V Troubleshooting and Specifications Troubleshooting 187 Product Specifications 193 ...
Page 186: ...186 ...
Page 192: ...Chapter 18 Troubleshooting P 660W Tx v2 User s Guide 192 ...
Page 200: ...200 ...
Page 208: ...Appendix A Pop up Windows JavaScripts and Java Permissions P 660W Tx v2 User s Guide 208 ...
Page 226: ...Appendix C Common Services P 660W Tx v2 User s Guide 226 ...
Page 232: ...Appendix D Legal Information P 660W Tx v2 User s Guide 232 ...