ForeRunner ATM Switch Network Configuration Manual
8 - 11
Security
Sec
u
rity
8.2 IP Filtering
The IP filtering feature lets the network administrator limit access to the control port of the
switch to prevent unauthorized access to the switch. The switch performs filtering on incom-
ing IP packets by determining if there is a match between the packet’s header source address
and this table of authorized incoming IP addresses. If the addresses match, the packets are
accepted, provided that they meet the requirements set up by the other IP filtering flags; oth-
erwise, they are rejected. Statistics are kept of the number of rejected IP packets and about the
last IP packet that was rejected.
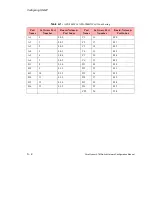
8.2.1 Authorized IP Address Table
Using the
conf
security
ipaccess
accept
command, the administrator can create an
entry in a table of authorized IP addresses from which IP packets will be accepted. When the
administrator creates an IP address entry in the table, he or she can apply a mask to specify a
wildcard range of allowable addresses. For example, an IP address of 163.26.54.6 with a mask
of 255.255.255.255 means only address 163.26.54.6 is accepted against that entry. However, an
IP address of 163.26.54.6 with a mask of 255.255.0.0 means addresses 163.26.*.* are accepted
against that entry. The table can contain a maximum of 32 entries.
The administrator can also delete entries from the table and display the contents of the table.
The table will persist across a reboot. (See the AMI Configuration Commands Reference Manual
for more information.)
CAUTION
When the authorized IP address table is empty,
all addresses are accepted. This is the default
state. Therefore, it is recommended that at least
one address be entered into the table. Otherwise,
anyone may access the switch via the control
port. The address you enter must be the address
of the machine you are using. Otherwise, you
will lock yourself out of the switch.
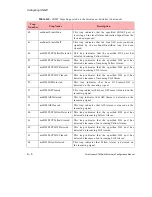
8.2.2 IP Filtering Flags
There are three IP filtering flags that can be configured to limit IP access in other ways:
ssr
,
lsr
, and
all
. These flags are set to
allow
or
disallow
IP packets using the
conf
security
ipaccess
ssr
,
lsr
, and
all
commands. (See the AMI Configuration Commands
Reference Manual for more information about these commands.)
Summary of Contents for forerunner series
Page 6: ......
Page 16: ...TOC 10 ForeRunner ATM Switch Network Configuration Manual Table of Contents ...
Page 20: ...LOF 4 ForeRunner ATM Switch Network Configuration Manual List of Figures ...
Page 22: ...LOT 2 ForeRunner ATM Switch Network Configuration Manual List of Tables ...
Page 30: ...viii ForeRunner ATM Switch Network Configuration Manual Preface ...
Page 144: ...3 58 ForeRunner ATM Switch Network Configuration Manual Configuring an Emulated LAN ...
Page 180: ...6 12 ForeRunner ATM Switch Network Configuration Manual ATM Forum PNNI ...
Page 220: ...9 6 ForeRunner ATM Switch Network Configuration Manual Configuring Timing ...
Page 300: ...D 24 ForeRunner ATM Switch Network Configuration Manual Configuring FramePlus Modules ...
Page 308: ...Acronyms 8 ForeRunner ATM Switch Network Configuration Manual Acronyms ...
Page 346: ...Glossary 38 ForeRunner ATM Switch Network Configuration Manual Glossary ...
Page 352: ...Index 6 ForeRunner ATM Switch Network Configuration Manual Index ...